WordPress is designed to be secure and reliable. Yet because of the sheer number of WordPress users, the content management system (CMS) is a common target for cyber threats. If you want to protect your site, a web application firewall for WordPress is a must-have tool.
A web application firewall (WAF) is a type of software designed to stop multiple types of cyberattacks. It filters traffic to and from your website to protect it from harm. A properly configured WAF is often the best line of defense against malicious actors.
In this detailed guide, we’re going to discuss how WAFs work and what makes them different from traditional firewalls. We’ll also discuss the benefits of using a WAF for WordPress, and introduce you to Jetpack Security’s WAF solution.
What is a web application firewall?
A WAF is software that sits between client applications and web servers. The WAF filters all incoming and outgoing traffic, looking for suspicious activity and malicious requests. If the WAF finds such activity, it will block it, which helps protect your website.
It’s important to note that WAFs work using sets of preconfigured rules. That means you need to set up the software to block specific types of traffic and activity. Alternatively, your web host or network administrator will do this for you if you have a package that includes a WAF.
If you’re paying for secure or managed WordPress hosting, your plan probably gives you a WAF. In most cases, you won’t have access to its configuration options or settings, so you depend on other people to update it and protect your website.
Leaving the control of a WAF in someone else’s hands is not necessarily a downside. Depending on your web host, they may employ security experts that track WordPress threats. It’s their responsibility to keep the WAF rules up to date, so your website is protected from the latest exploits.
How WAFs differ from traditional firewalls
There are several differences between WAFs and traditional firewalls. To start with, these solutions tackle different security issues, and they work at different levels.
A WAF is designed to work with web applications. Typically, WAFs focus on defending a website against cyberattacks like SQL injections, cross-site scripting (XSS), and other attacks that target known vulnerabilities.
A traditional firewall can also help protect web applications. But in a lot of cases, these firewalls focus more on monitoring traffic than behavioral patterns, which is one of the ways in which WAFs can detect specific types of attacks.
To put it another way, a traditional firewall can be useful if you want to block certain IP addresses or close specific ports to traffic. Meanwhile, a WAF will perform better if you’re trying to protect your site against common types of cyberattacks, even if you don’t know what IPs to blocklist.
These solutions are also different in where they fit into the network stack. A WAF is designed to work in front of the web server, to monitor traffic right before it reaches your website. Traditional firewalls, on the other hand, can work at multiple levels of a network. You may have some firewalls that monitor traffic within a network, and others that focus on outgoing traffic.
If you run a WordPress website, you can benefit from setting up a web application firewall. If your business runs an internal network, you may also want to consider adding regular firewalls to your security stack.
Understanding how web application firewalls detect and prevent threats
Now that you have a better understanding of how WAFs work, it’s time to talk specifics. That means discussing the ways in which WAFs are capable of detecting threats.
This is essential information because not all WAFs offer the same level of security or configuration options. If you use a WAF that allows you to access its settings, you’ll want to know how these processes work before you make any changes to them.
1. Signature-based detection
A WAF can detect specific types of cyberattacks in many ways. When a WAF analyzes traffic, it looks for patterns and behaviors that can help it identify malicious activity. This is called signature-based analysis, and it relies on databases that include information about past attacks.
These databases maintain information like signatures and patterns. That means a WAF should be able to detect new attacks if they have requests or headers that are similar to past events.
The best way to understand attack signatures is to think of them as fingerprints. Every request sent to your website will include unique identifiers.
In the case of malware, these signatures can be specific parts of the code. With attacks like SQL injections, the WAF might be able to identify patterns in the HTTP requests.
Maintaining the type of vulnerability and attack database needed to conduct signature-based analysis is outside of the abilities of most users, even if you have experience with network security. That’s why using a third-party solution can be much more efficient, both for personal and business websites.
2. Anomaly-based detection
Next, let’s talk about anomaly-based detection. This method relies on configuring the WAF to establish a baseline of what constitutes ‘regular use’ of a web application or website. For instance, the WAF might be configured to act when it detects unusual spikes in traffic within a short timeframe.
Those spikes in traffic would be considered an anomaly because it’s not something that happens commonly on the site. Depending on the WAF’s configuration, it might block that traffic if it matches with other attack patterns, like direct denial of service (DDoS) events.
How effective a WAF is at detecting anomalies will depend entirely on its configuration. What’s normal for one site, like getting thousands of hits in a matter of hours, might not be common for others. That’s something to consider if you’re able to set up new rules for a firewall.
3. Behavioral-based detection
Depending on the solution you use, the software should be able to detect client behavior that doesn’t fit within regular parameters. In many cases, WAFs will refer to anomaly and behavioral-based detection techniques interchangeably.
To give an example, if you have a significant number of login attempts from the same IP address, that can constitute exceptional behavior. A few attempts in a short time frame can simply indicate a user who has forgotten their password. On the other hand, if there are dozens of attempts to access the back end, you might be dealing with a bot or a hijacked account.
Where anomaly-based detection focuses on the site as a whole, behavioral analysis looks more at the actions of end users. A WAF can draw on data about how users behave on other websites to find suspicious patterns of activity, and help you protect your website or application.
The main challenge when it comes to behavioral-based detection is that it can lead to false positives. A WAF may flag regular user activity as malicious because it fits into patterns that it’s trained to detect.
This might not happen often, but if it does, it’s worth considering that user behavior is not static. Users can and will modify how they interact with your website for many reasons, including as a response to updates.
Five benefits of using a WAF for WordPress sites
Web application firewalls are incredibly sophisticated software solutions, and implementing one doesn’t need to be complicated. If you use WordPress, there are plenty of plugins, services, and even web hosts that can help you protect your website using a WAF with minimal setup required.
On top of being easy to implement, there are many benefits to using a WAF to protect your WordPress website. Here are five of the top reasons to consider taking this step.
1. Protection against SQL injection, XSS, and other attacks
The main benefit of using a WordPress web application firewall is protection against some of the most common attacks, including SQL injection attacks, XSS scripting, and more.
This is thanks to a WAF’s signature-based detection abilities. Many attacks come from similar sources and behave the same as other types of instructions.
If your WAF maintains a database of vulnerabilities, past attacks, and known malicious actors, it will have access to those signatures. This means it can compare potentially malicious traffic against past events, to see if it detects similarities that are red flags.
The more well-known an exploit, the more effective a WAF should be at mitigating or blocking it. Still, its success will greatly depend on how the firewall is maintained and configured, and on whether it pulls from an up-to-date database of vulnerabilities.
Jetpack Security (a WordPress security solution that we’ll discuss more shortly) relies on the most comprehensive database of WordPress vulnerabilities and attack vectors — WPScan. This keeps your website secure, as the database is constantly updated by security experts and WordPress developers.
2. Mitigation of zero-day exploits
By definition, a zero-day exploit is an unknown type of attack. That means conventional security solutions might not be prepared to block it.
Web application firewalls have an edge when it comes to protecting your website from zero-day exploits. For one, if the exploits include signatures similar to other attack vectors, that can alert the firewall that it’s dealing with a potential attack.
Zero-day exploits might also trigger anomaly detection rules. If the exploit causes anomalous patterns of activity or traffic on your website, a WAF can block the corresponding requests for the sake of prevention. This might affect normal traffic and site usage, but it can be worth the downsides if it helps you protect your site against these unknown types of attacks.
3. Custom IP address rules
Depending on the WAF solution you use, you might have control over specific IP address rules. That means you can either allowlist or blocklist IP addresses depending on your WAF settings.
Allowlisting IPs means that only the addresses on that list will be able to access either the website as a whole or specific parts of it. Some WordPress websites use this functionality to allowlist the IP addresses that can log in to the dashboard and make changes.
Blocklisting IPs, on the other hand, means that the addresses on that list won’t be able to connect to the site. This approach blocks addresses that are known to engage in cyberattacks or other types of security breaches.
Jetpack Security offers the option to both allowlist and blocklist IP addresses. This gives you a greater degree of control over who can access your website, without compromising the existing WAF rules.
4. Downtime prevention
One of the most significant ways cyberattacks can impact your website is by causing downtime. Attacks can overwhelm the server, break critical site components, or cause errors that block access.
A WAF can help you prevent downtime by mitigating or blocking attacks altogether. Since the WAF analyzes traffic before it hits your site, it can be highly effective in preventing scenarios that result in downtime.
5. Compliance with data protection regulations
Depending on your jurisdiction, you might be under an obligation to fulfill specific security requirements. One example of this is the general data protection regulation (GDPR).
The GDPR requires you to inform the appropriate regulatory authority if your website is the victim of a data breach and contains information about users from the European Union. This is to protect sensitive user information and avoid the possibility of websites and businesses sweeping security breaches under the rug.
Using a WAF doesn’t mean you can ignore regulations. It means your website is better protected against security incidents that can put you in breach of these rules.
A properly configured firewall can prevent a lot of cyberattacks. That means your users are safer, and you lower the risk of having to pay fines.
Jetpack Security: WordPress WAF and other comprehensive security tools
If you’re looking to improve WordPress security, and you want a solution that’s easy to use and includes WAF functionality, Jetpack Security is a great option. Let’s dive deeper into what this security plan gives you.
We guard your site. You run your business.
Jetpack Security provides easy‑to‑use, comprehensive WordPress site security, including real‑time backups, a web application firewall, malware scanning, and spam protection.
Secure your site1. Enterprise-grade WAF for real-time threat defense
When it comes to firewalls, data is king. The service with the most comprehensive set of information on known vulnerabilities, malicious actors, and other threats to WordPress will provide the best protection.
Jetpack Security leverages the most advanced list of WordPress vulnerabilities — provided by WPScan — to help protect your website from threats. You get access to an enterprise-grade web application firewall at consumer-level prices. Moreover, setting up Jetpack Security is relatively simple, and its WAF comes pre-configured so you can start benefiting from it immediately.
2. Automated, real-time malware scanning with one-click fixes
If an attack gets past your WAF, it can infect your website with malware. WordPress malware is also common if you download plugins or themes from untrustworthy sources. This can infect your site, and even affect your visitors depending on the type of malware.
In these situations, your primary goal should be to identify the malware and remove it as soon as possible. Jetpack Security can help you do this, as it automatically scans your site.
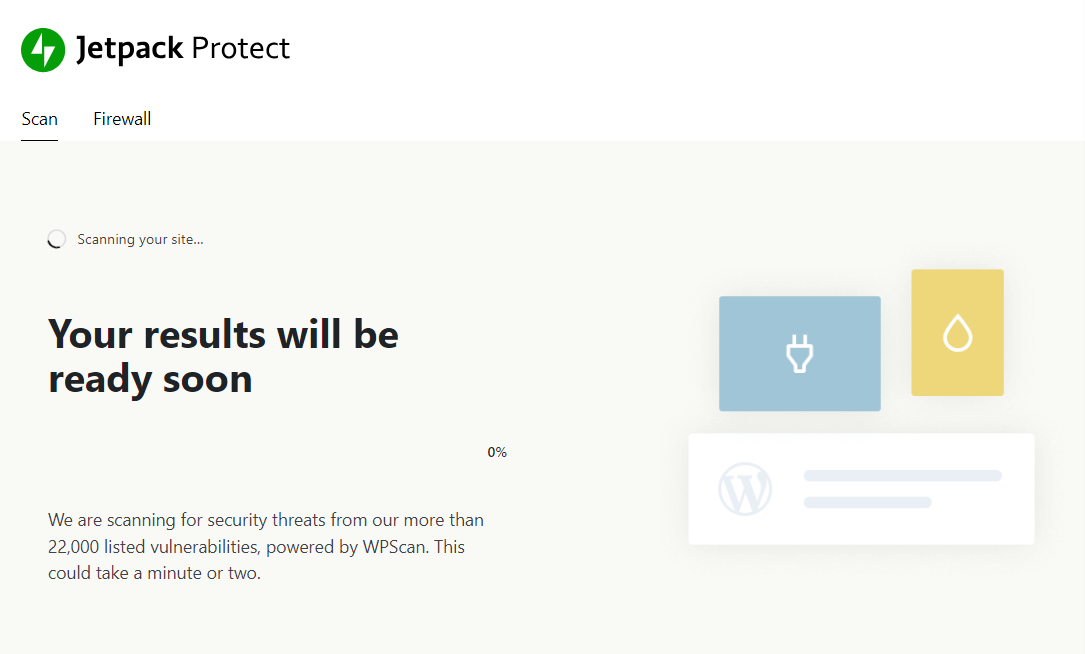
If Jetpack detects malware, you’ll likely be able to use the one-click fix function to remove it without having to dig into your site’s files. Jetpack Security is exceptional in this regard because it can scan your website against a massive database of WordPress vulnerabilities (which also makes the WAF more effective).
3. Automatic brute force attack protection
Brute force attacks involve trying lots of credentials to gain access to your website. This type of attack is possible if you don’t have security measures to block malicious actors from accessing your website via the WordPress login page.
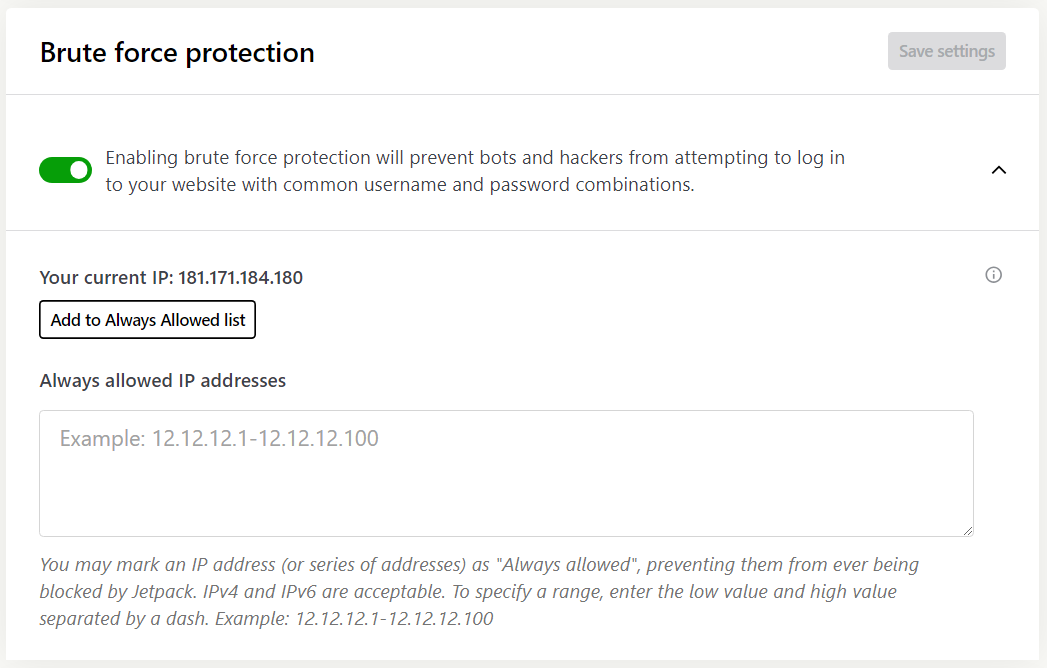
By default, Jetpack Security will protect your website from brute force attacks. You can also configure it to allowlist specific IP addresses. This can help prevent the rare situations where Jetpack will block a user for repeatedly trying to access their account simply because they forgot their credentials.
4. An activity log to monitor suspicious activity
Having access to an activity log is one of the best measures you can implement for WordPress security. An activity log is a record of what happens on your website, and it can track all sorts of events depending on which tool you use.
The Jetpack activity log can help you keep tabs on changes to pages and posts, new file uploads, plugin and theme installs, and more. All of this information can be incredibly useful when troubleshooting issues on your website.
If you encounter technical problems, your first course of action should always be to check the security logs to see what changes have been made to the website. Jetpack activity logs include information about when each event occurred and which users were involved, which will enable you to see what (or who) caused the error you’re trying to fix.
5. Downtime monitoring and incident response
Although downtime should be rare, it’s important to prepare for it. Jetpack Security can help you with this, thanks to its system of downtime notifications.
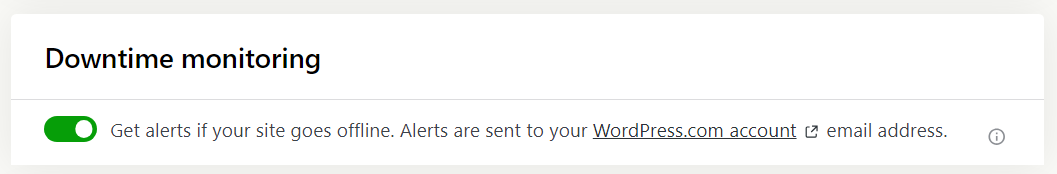
If you use Jetpack and your website becomes inaccessible, you’ll get a notification via email. This means you can jump into action to troubleshoot your site and solve the issue that caused the downtime.
6. Real-time backups and one-click restores
Having a recent backup of your site is the best way to troubleshoot many technical and security issues with WordPress. If your site is attacked, you should be able to easily restore it to a previous state without losing much (or any) data.
Jetpack Security offers real-time backups. That means it creates copies of your site any time you make changes to it. This gives you a lot of control over restore points, as opposed to creating backups on a set schedule.
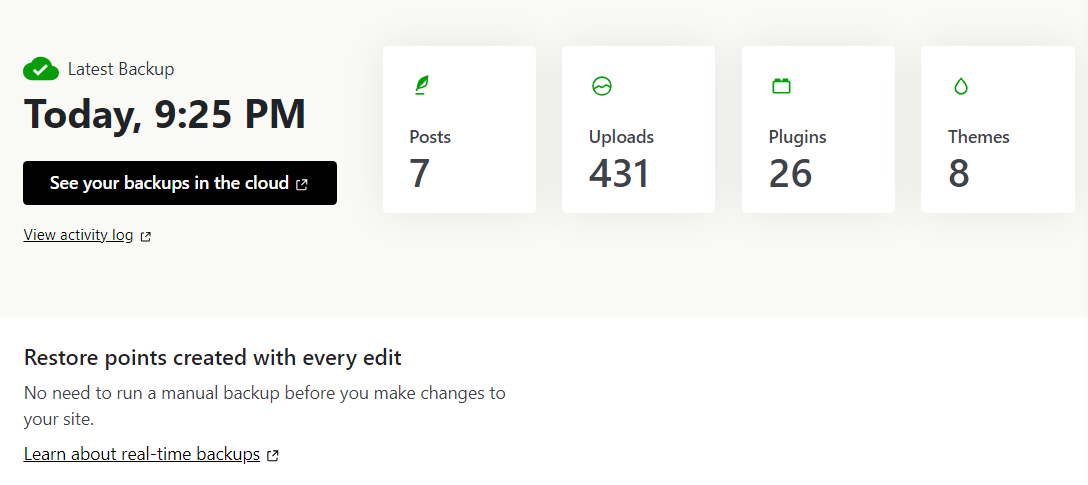
Jetpack Security also offers one-click backup restoration. You can manage backups directly from Jetpack without having to access the dashboard. This can be critical if you lose access to the WordPress admin area due to a security breach.
How to install and configure the Jetpack Security WAF
Now, let’s go over how you can install and configure Jetpack Security and its web application firewall. The process is very straightforward.
To get started, install Jetpack in the WordPress dashboard by navigating to Plugins → Add New. Use the search feature to look for Jetpack, and click on Install Now.

Note that you’ll see several Jetpack plugins available in the WordPress repository. Install the main Jetpack option and activate it. This will prompt the plugin to ask you to connect to WordPress.com, for which you’ll need an account.
After connecting Jetpack with your WordPress.com account, go to Jetpack → My Jetpack and look for the Activate a license option.
On the next screen, you’ll see a field where you can enter your Jetpack Security license. You can get a license by subscribing to a Jetpack Security plan.
Once you enter the license and click on Activate, this will unlock Jetpack Security features. To access the WAF settings, go to Jetpack → Protect → Firewall.

The firewall is enabled by default. You can also toggle the brute force protection and allowlist settings. If you click on Edit manual rules under Enable manual block and allow lists, you’ll be able to enter the IP addresses you want to blocklist or allowlist.

As you can see, Jetpack is designed to require minimum configuration. You can simply enable Jetpack Security and the firewall will start protecting your site right away. At the same time, you can customize the settings to meet your specific needs.
Frequently asked questions
Still have questions about how web application firewalls and Jetpack Security work? We’ve got you covered.
What does a web application firewall (WAF) do for a WordPress site?
A WAF helps filter traffic to your WordPress website. The firewall can identify malicious attacks and mitigate or stop them, depending on its configuration.
What specific security vulnerabilities in WordPress does a WAF mitigate?
A WAF can stop several kinds of attacks targeting your WordPress website. Some examples include SQL injections, cross-site scripting, and DDoS attacks. What types of attacks a WAF can mitigate will depend on its rule set.
How does Jetpack Security differ from other WAF services?
Jetpack Security is different from other WAF services because1111 it gives you much more than just a firewall. It’s a comprehensive suite of security tools to protect your website. These tools include brute force protection, real-time backups, malware scanning, an activity log, and spam protection.
Is it difficult to configure Jetpack Security’s WAF for someone who is not technically savvy?
Jetpack is designed to be easy to configure. You can activate Jetpack Security, and its web application firewall will start working right away using rules that are regularly updated. The same applies to the Jetpack Security brute-force protection feature.
Where can I learn more about Jetpack Security?
You can visit the official Jetpack Security page and read more about what it offers. You’ll also be able to compare Jetpack plans and decide which option fits your needs best.
Protect your WordPress website using a WAF
Advanced security measures can safeguard your site against data breaches and hacking events. They can also protect user information and keep visitors happy. A sophisticated WAF can filter out and block suspicious IP addresses, malicious users, and more.
With Jetpack Security, you get to use a WAF that’s backed up by one of the most comprehensive WordPress security databases in the world. This WordPress WAF can protect your website from common cybersecurity threats like DDoS and brute force attacks. Moreover, Jetpack is designed to require minimal configuration, which makes it simple to set up.
If you’re ready to try Jetpack Security, sign up today to access a WordPress WAF, real-time backups, malware scans, and other advanced security features!
We guard your site. You run your business.
Jetpack Security provides easy‑to‑use, comprehensive WordPress site security, including real‑time backups, a web application firewall, malware scanning, and spam protection.
Secure your site