Whether your WordPress website is a multi-million dollar ecommerce store or a personal blog, the negative effects of malware can be devastating. No matter how many preventative measures you take, you never know when someone might find and exploit a new security vulnerability.
Many types of malware don’t disturb the day-to-day functioning of your website, so you might not even know you’ve been compromised. While the malware is hidden away, it’s quietly stealing sensitive data, inserting spam links to harmful websites, adding malicious redirects, sending scam emails to your visitors, or using your server to mine cryptocurrency. It may take you weeks or months to discover that something is awry and, by then, you’ve been blocklisted from search engines, lost user trust, and started an arduous scramble to recover data.
The first step in preventing malware infections is to implement stringent security measures. The next step is to install a malware scanner like Jetpack Scan to catch some of the more common types of malware and remove them before there’s any extensive damage.
In this article, we’ll talk about how malware scanners work and why they’re important to the security of your website. We’ll also debunk some common myths about malware scanners, discuss factors to consider when choosing a solution, and show you how to install a malware scanner on your WordPress site.
What is a website malware scanner?
A website malware scanner is designed to identify malicious code and software, commonly referred to as malware, on a website’s server. They scan the files and directories on a server and search for characteristics, behaviors, and known malware patterns, commonly referred to as signatures, that may indicate the presence of malware.
These scans are usually done in consistent periodic intervals, to provide continual monitoring for malicious files and activities on a server. At the very least, this approach can minimize the harm caused by malware, but in many cases it can detect and block malware before it can be executed or cause damage.
When a malware scanner identifies malicious code, it typically offers options for dealing with the threat. This may include quarantining the infected file, attempting to clean it, or notifying the web admin for manual removal.
Is a malware scanner worth it for WordPress sites?
Even with good security practices, your site may still be hacked. No solution is perfect and hackers are always hard at work coming up with new ways to breach websites and evade detection.
If the biggest global players still periodically have to deal with hacked websites, there’s no reason to think your site is 100% impenetrable. Good security practices will greatly reduce your risk, preventing a significant majority of hacks. However, if something does slip through, a malware scanner can help by quickly identifying and eliminating those threats.
By identifying malware quickly, you can protect the reputation of your WordPress website and maintain solid site performance. If malware is allowed to run unchecked on your website, it can lead to search engine penalties or blocklisting. It can also slow down your site speed by using your server’s resources to run malicious software.
The role of malware scanners
Malware scanners play an important role in the security ecosystem. If malware makes it past a website’s first line of defense and can penetrate a site, scanners serve to help experts mitigate potential damage by taking immediate action. Let’s look a bit further into the role of malware scanners.
Early threat detection
Malware scanners can preemptively look for known vulnerabilities in extensions, alerting the user to update or apply the needed fixes. Some additional vulnerabilities scanners might alert you to include:
- Insecure user passwords
- Out of date plugins and themes
- Outdated or misconfigured WordPress core files
- Blocklisting
- Suspicious site activity
Streamlined cleanup processes
Some malware scanners will include an option to remove malware automatically or provide you with reports on infected WordPress files or directories so that you can easily find and remove any offending code.
Integration with other security measures
Malware scanners are an important component of a layered security strategy — sometimes referred to as a Swiss cheese model of security. No individual security measure is enough to keep your website safe. There will always be some hole where an attacker can get through. By employing a Swiss cheese strategy, you create multiple layers of protection that, when used together, provide a more complete defense.
If your malware scanner comes as part of a broader security software package or is compatible with other security tools that you use, then you’ll have an added layer of malware protection for your website.
Debunking common myths about WordPress malware scanners
Myth 1: Scanners offer a false sense of security
Malware scanners should never be considered a sole method of website security. Any security software that promises that you only need a malware scanner for complete security should be avoided. The same goes for any security software company that says malware scanning is unnecessary.
Think of it this way — if you keep your doors and windows locked, an intruder could still break in. You could build your home in a cave underground with only one entry and exit, surrounded by multiple rows of fencing, a moat full of alligators, and a series of complex booby traps.
But not only is that impractical for most homeowners (and definitely against most HOA rules), it would be pretty off-putting for invited guests and an intruder may still be able to find a way in anyway.
A reasonable approach might focus on secure locks on all windows and doors, keeping valuables hidden in a locked safe when you’re away, and then installing security cameras outdoors to catch any intruders that trespass on your property or attempt to gain entry to your home.
This same approach holds true for website security. The only way to make your website 100% safe would be to prevent anyone but you from accessing it (and that sort of defeats the purpose of having a website). You’ll always need to balance security with usability, and what that looks like will vary depending on your needs.
Focus on the preventative measures that have the biggest impact on security, then install a malware scanning plugin to catch the most common threats and security vulnerabilities that might slip through.
Myth 2: All scanners are equal
Not all WordPress malware scanners work the same way or offer the same features. There are also cost differences and, within each software provider’s offerings, there may be different tiers of service at different price points.
Here are some ways in which malware scanners might differ:
- Scanning methods. Malware scanners can use different techniques for scanning WordPress websites. Some rely on signature-based detection, heuristic analysis, or behavioral analysis, while others use a combination of these methods.
- Real-time monitoring. Some WordPress malware scanners provide real-time monitoring, continuously checking for malware and suspicious activities on your website. Others offer scheduled or on-demand scans.
- Database and file system scans. Malware scanners may scan both the website’s database and file system for malicious code and files. The depth and thoroughness of these scans can vary.
- Removal capabilities. While most malware scanners can detect malware, not all of them offer automated or manual removal options. Some may only alert you to the presence of malware and leave the removal process to website administrators.
- Ease of use. The user interface and ease of use can vary between different WordPress malware scanners. Some offer user-friendly dashboards and detailed reports, while others may have a steeper learning curve.
- Integration. Certain WordPress malware removal plugins and scanners are designed to work seamlessly with specific WordPress security services, making integration easier for WordPress users.
- Compatibility. The compatibility of a malware scanner with your WordPress setup (including your hosting platform, the version of WordPress, plugins, and themes you’re using) can vary. Some scanners may have limitations or compatibility issues.
- Resource usage. The impact on your website’s performance and server resources can differ between malware scanners. Local scanners will consume more resources than remote scanners, potentially affecting your site’s speed and responsiveness.
- Cost. While some malware scanners offer a free version, others are premium tools or services that require a subscription or one-time payment. The pricing structure and features can vary widely.
- Support and updates. The level of customer support and the frequency of updates provided by the malware scanner’s developers can differ, which can be crucial for maintaining the effectiveness of the tool.
- Additional features. Some malware scanners may include additional security features such as firewall protection, vulnerability scanning, and blocklisting checks, while others focus solely on detecting malware.
Since there are a lot of differences between scanners, it’s important to do some thorough research so that you can choose a malware scanner that suits your specific needs, budget, and technical requirements.
Myth 3: Scanners slow down websites
Yes, local scanners can be resource intensive, but even still, you can set these scans to run at times when you typically get the least amount of web traffic.
There are a lot of other things that will slow your site down more consistently than even periodic scans from a local malware scanner. A few of the most common culprits for a slow website are:
- Low-quality hosting. If your WordPress website is hosted on a low-quality, hosting plan with limited storage, memory, and CPU resources, you’ll experience slow load times. If it’s on a shared server, you won’t know if your “neighbor” sites are set up efficiently, infected with malware, or performing tasks that eat up tons of server resources.
- Large image and video files. If your image file sizes aren’t optimized to be as small as possible (while retaining the quality you need) they can slow down the load time of your website. Video files can also eat up a lot of server resources and are best hosted off-site by a service like Jetpack VideoPress that’s designed to more efficiently deliver video content.
- Lack of caching. Caching improves website performance by temporarily storing and serving preprocessed content from the web server so it can be quickly retrieved and delivered to users without the need to regenerate the content from scratch each time a request is made. This reduces the strain on the server and minimizes the time it takes to load web pages.
- Unoptimized code. Techniques like code minification, compression, and asynchronous or lazy loading can help to dramatically improve performance.
- Plugin and theme bloat. Using poorly coded themes and plugins, too many plugins, or redundant plugins can all contribute to slowing down your website.
- Not using a content delivery network (CDN). A CDN is a distributed network of servers strategically placed in multiple geographic locations with the goal of delivering web content to end users more efficiently and with improved performance. CDNs are designed to reduce latency, minimize the load on the origin server, and enhance the overall user experience.
If you’ve done all you can to optimize the speed of your site, and you want to ensure that it loads quickly at all times, opt for a WordPress malware scanner that uses remote scanning. Remote scanners use their own server resources to perform scans so that there’s little to no impact on your own server.
Regardless of what kind of scanner you’re considering, you can be sure that there’s one thing that will slow down your site more than a malware scanner — actual malware.
Myth 4: If malware can disable your scanner plugin anyway, there’s no point in installing one.
The main problem with just about every malware scanner solution for WordPress websites is that they require installing a plugin to use. And if some extra sneaky malware or any hacker that gets admin level access can simply waltz in and delete your malware scanner plugin, then why bother? What’s the point?
The truth is that just because malware scanners aren’t perfect doesn’t mean that they aren’t useful and a key component of a comprehensive, layered approach to website security. Using a high-quality malware scanning service in conjunction with other preventative security measures will provide you both the best protection and response capabilities.
How to quickly respond to suspected malware
If you’re worried about your security plugin being deleted by a bad actor, here are a few things you can do that make it easier to react quickly:
- Use a malware scanning service that will send you alerts when your connection to their service is disrupted. At the very least, your service should email you a notification if it can’t connect to your website.
- Create a filter for emails from your security software company. Flag them as high-priority or important to make sure they don’t accidentally end up in your SPAM folder.
- Get immediate notifications to your phone when service is disrupted. Make sure the security software company you choose offers push notifications or SMS alerts so you can get updates to potential problems as quickly as possible.
- Use an activity log that’s hosted off site. Make sure that your security service offers activity logging and that the log is kept on separate servers from your website so that it will be accessible even if your website becomes compromised. You should be able to review the log to find unusual activity that might indicate when your site was hacked.
If you log in to your site and find that your scanner has been disabled or deleted, here two different options for next steps:
- Restore from a clean backup. If you know that your site was not infected on a certain date, you can restore your website from a previous backup taken on that date. If your web host keeps daily backups, you can restore from those, or you can use a plugin like Jetpack VaultPress Backup that works in real time for the most comprehensive protection and stores files off-site for enhanced security and reduced strain on your resources.
Note: If you have an ecommerce site with orders that have been placed since your last clean backup, or if you have published new posts or products, you may lose that data when restoring your backup. You’ll want to make sure to export any files, customers, posts, products, and orders before restoring from your backup so you can re-import them.
This is, again, where Jetpack Backup shines. It retains WooCommerce order data, even if you have to restore the rest of your site to a date before recent orders were placed.
You’ll want to examine your exported files to make sure there are no traces of malware hidden in them. You can do this by restoring your backup and exported files on a staging site and performing a scan before deploying to your live environment.
- Install a fresh copy of your security plugin and run a scan. If you don’t know when the hack occurred, then you should delete the security plugin and reinstall a fresh copy directly from the WordPress.org library or the developer’s website. In case the security plugin itself was compromised, this should overwrite any changes that were made to the plugin.
Then, run a scan of your site. If the scan detects malware, you can either have the scanner remove it or fix it manually.
If you run a scan and no malware is detected, but you are still concerned that something suspicious is going on, follow the steps in our article, How to Detect and Remove Malware from a WordPress Site. There are also some great steps included at the end of that article for what to do after malware has been removed to protect against future attacks.
Five factors to consider when choosing a malware scanner
1. Is it a local scanner or remote scanner?
Some scanners operate locally on your own server and some operate on remote servers. There are some key differences you should be aware of between local scanners, entirely remote scanners, and remote scanners that integrate with your WordPress site using a plugin.
Local scanners
Local malware scanners are installed directly on the web server where your WordPress site is hosted (via a plugin) and run within that server environment. They focus on deep scanning and monitoring of WordPress files, directories, and databases. They can provide real-time monitoring or can be set to scan at specific intervals to alert website owners to suspicious changes or activities.
Since local scanners have access to your files and directories, some may also offer automated clean up of malware infections.
A drawback to local scanners is that they can consume more server resources than remote scanners, potentially impacting website performance. This is especially important to consider if your website is located in a shared hosting environment, which may have limited resources available.
Additionally, because the local scanner and the malware run within the same environment, the malware can directly attack the scanner and allowlist the malware so that it’s not flagged as suspicious.
Remote-only scanners
Remote malware scanners are hosted externally by a third-party security service provider. They operate from a server that is separate from your host. Since the data they compare against while scanning your site is on an outside server, any malware that might be installed on your site won’t be able to make changes like trying to allowlist itself.
Purely remote scanners (e.g. browser-based services where you type in the URL of your site and perform a manual scan) don’t have direct access to your website’s file system or database like a local scanner would, so they can only check for any vulnerabilities and evidence of malware through publicly accessible parts of your website. This means that there are plenty of site components that they can’t review at all.
Integrated remote scanners
Most remote scanners designed specifically for WordPress websites rely on installing a plugin that establishes a secure connection to your site with permissions that allow for deep directory access.
This approach has the following benefits:
- A reduced impact on site performance during scans. Having most or all of the scanning process take place remotely allows for scans without slowing down your website.
- Deep scanning of files and directories and automatic cleanup. Having a local component to your remote malware scanner means that your scanner will have file and directory access that allows for deep scanning and automatic malware cleanup. This improves your chances of detecting malware and removing it quickly.
- Scans that are compared against the most up-to-date databases. When databases of known malware are hosted off-site by your provider, your scans are always being compared against the latest available information even if your plugin is out of date.
- Off-site logging. Since your scanner is gathering information with a remote server, that information can also be stored remotely. This way you’ll still be able to review all your activity logs in case you lose access to your website due to a malware infection (or any other reason).
A scanner that uses this hybrid approach is probably going to be your most efficient and robust option.
2. Does it have a web application firewall (WAF)?
While malware scanners and WAFs serve different primary purposes, they complement each other effectively to provide comprehensive protection against various threats.
Combining a WAF with a malware scanner ensures a more comprehensive defense. WAFs are designed to block and mitigate a broad range of threats, including malicious traffic, suspicious requests, and common web application attacks like SQL injection, cross-site scripting (XSS), and cross-site request forgery (CSRF). If you do end up with a hacked WordPress site, a WAF can prevent malware from spreading by blocking malicious requests that it makes.
Another benefit of WAFs is that they offer real-time monitoring and protection by inspecting incoming web traffic and blocking threats as they occur. WAFs are also equipped to protect against zero-day vulnerabilities and emerging threats by identifying suspicious patterns and behaviors. If a new malware strain or attack technique emerges, the WAF can often detect and block it before the malware scanner has been updated to recognize it.
By integrating a malware scanner with a web application firewall, you create a layered defense strategy that addresses various aspects of web security, from malware detection and removal to proactive threat prevention and mitigation.
3. Who developed and manages the scanner?
It’s essential to know that you can trust the developer of the security software you are using. You want your security software to be top-notch, well maintained, and be designed specifically to work with WordPress.
When evaluating a malware scanner software company, consider asking the following:
- Are they an established and reputable developer? Reputable developers actively maintain their tools, releasing updates to address new threats and vulnerabilities. Knowing the developer allows you to assess the tool’s commitment to ongoing support and improvement.
- Do they have a deep understanding of WordPress security? Knowing the developers and their reputation in the WordPress security community can help you determine if the scanner is trustworthy and reliable. Developers whose product specifically targets WordPress sites, and who have a long history of working with WordPress, are more likely to create and maintain effective and secure tools for WordPress.
- Are they committed to transparency and privacy in data handling? Malware scanners have access to sensitive information about your website, including files and database contents. Transparency regarding data usage and storage practices can provide you the information you need to know if your data is being handled securely.
- Are they respected among users? Developers with a strong online presence often have active user communities. Checking user feedback and reviews can provide insights into the effectiveness and reliability of the malware scanner.
- Do they have a high level of customer support? When it comes to urgent security issues, you want to be able to easily reach out for technical support, questions, or assistance if you encounter a problem. Make sure your malware scanner developer offers the support you need.
Understanding the developers and administrators behind your WordPress malware scanner is crucial for ensuring the tool’s legitimacy, security, and effectiveness. Reputable developers with an extensive background in WordPress security plugins are more likely to provide reliable and secure solutions, offer timely support and updates, and be transparent about their data handling practices. When selecting a malware scanner for your WordPress site, it’s wise to research the developers and their track record to make an informed choice.
4. How much does it cost vs. the financial impact of an attack?
The cost of a WordPress malware scanner can vary widely based on several factors, including the features, capabilities, and the provider you choose. Some general pricing tiers for WordPress malware scanners include:
- Free plugins. There are several free malware scanner plugins available in the WordPress Plugin Directory. These plugins offer basic malware scanning features at no cost. While they can be useful for simple scanning needs, they may lack advanced features and support.
- Premium plugins. Premium WordPress malware scanner plugins typically offer more advanced features, more frequent scanning, automated cleanup, and additional security measures. Prices for premium plugins can range from around $100 to $500 or more per year, depending on the features and the number of websites you want to protect. Some premium plugins also offer a free version with limited features if you want to try the software for a while before deciding to upgrade.
- Enterprise solutions. A large organization with a complex WordPress website and high-security requirements may opt for custom enterprise solutions. Pricing for these solutions varies significantly and is typically negotiated with the provider based on specific needs, including the number of websites, customizations, and service-level agreements (SLAs).
- One-time scanning services. Some companies offer one-time scanning and cleanup services for a fixed fee. Prices for one-time scanning and removal services typically range from $50 to $200 or more, depending on the complexity of the cleanup and the size of the website.
It’s important to consider your website’s specific needs and budget when choosing a WordPress malware scanner. While a free version of a security plugin may suffice for basic needs, premium plugins and subscription services offer more comprehensive security features and support.
5. Does it integrate well with other security solutions?
Securing your WordPress site involves a number of steps and is an ongoing process. It’s not something you can simply set and forget. Preventative measures such as real-time backups, web application firewalls (WAFs), brute force protection, strong passwords, two-factor authentication (2FA), strict permissions settings for accessing sensitive areas of your website, and other precautions are all important parts of keeping your website secure.
Malware scanners are just one part of that greater security ecosystem.
Some WordPress malware removal plugins or scanners stand on their own and may not be compatible with other security software that you’re using. Other malware scanners are integrated into broader-featured security plugins, or are one module within a suite of plugins from the same developer.
For instance, Jetpack Scan can be enabled on its own, but it’s also available as part of the popular WordPress security plan Jetpack Security, which offers:
- Malware scanning and removal. Jetpack will automatically scan your WordPress site, and you can remove most detected malware with a single click.
- Brute force attack protection. These attacks are malicious login attempts by bots that quickly cycle through combinations of usernames and passwords and submit them to your login form. If they can enter the right combination and gain access to your website, they can install malware, steal sensitive data, or shut down your site entirely.
Even if they don’t succeed, the repeated rapid-fire form submissions can create a spike in HTTP requests that can either slow your website down drastically, or cause the server to run out of memory, making your site non-responsive.
When Jetpack detects this type of bot activity, it will block that IP from accessing your login form and prevent excessive HTTP requests before they affect your site’s functionality.
- Downtime monitoring. Jetpack Security proactively and continuously tracks and assesses the availability and performance of your website, alerting you to any unexpected interruptions or periods of unavailability.
- A web application firewall (WAF). WAFs protect websites from online threats and attacks by acting as a barrier between web traffic and the website itself. It filters and monitors incoming and outgoing traffic to identify and block malicious activity.
- VaultPress Backup. Another important aspect of security is making and keeping regular backups of your website. If you keep regular backups of your website, you’ll be able to restore a previous, clean version of your site in the event your site does get a malware infection.
VaultPress takes real-time, automated backups of your site and stores them off-site on their own servers so they stay safe in case your server is compromised. - Akismet anti-spam protection. While comment spam is annoying, it’s often overlooked as a security threat. Comment spam usually adds unsolicited affiliate links for click farming purposes or SEO backlinking, but it may also include phishing links or malware. The spammer may even add your site to a list of spammable sites for other bots to use, and you’ll find yourself flooded with spam comments, spikes in HTTP requests, or your site may become a hub for watering hole attacks.
Akismet doesn’t require captchas or other user interface additions to identify spam and stop it in its tracks. It works silently in the background to block spam comments and form submission, so your visitors enjoy a frictionless experience.
Akismet has also been in the spam protection business longer than any other company and has the most comprehensive database in the world. And because the data being used is all stored in the cloud, Akismet has zero negative impact on site speed, bounce rates, and conversion rates.
No matter what malware scanner you choose, make sure it either includes the option of additional security prevention features or can work together with other plugins and security measures that you are using.
How to install and use a malware scanner on your WordPress site
Installing a malware scanner on your site can be as simple as going to Plugins → Add New in your WordPress dashboard, searching “malware scanner”, finding the right WordPress plugin for your needs, and clicking Install on the one you want to use.
You may have additional settings for your scanner that you’ll need to configure, and you can usually find those instructions on the plugin developer’s website, or they may be listed on the Details tab of the malware scanning plugin’s page in the WordPress Plugin Directory.
If you’re using a premium malware scanner, the developer should provide documentation on their website or with your purchase on how to install and configure your scanner.
For this example, we’ll show you how to install and enable Jetpack Scan.
We guard your site. You run your business.
Jetpack Security provides easy‑to‑use, comprehensive WordPress site security, including real‑time backups, a web application firewall, malware scanning, and spam protection.
Secure your siteInstalling Jetpack Scan
Jetpack Scan is a premium feature available through the Jetpack Protect plugin.
If you want a more comprehensive tool, you can access Scan alongside additional WordPress security features through a Security or Complete plan with the full Jetpack plugin.
During the checkout process you’ll be asked to create a WordPress.com account if you don’t have one already. Once you’ve made your purchase, you will be asked to select a site on which to install Jetpack Scan. If you don’t see your website listed, you’ll need to install the base Jetpack plugin on your website and connect it to your WordPress.com account. The main Jetpack plugin is required to use Jetpack Scan.
1. Installing Jetpack
Go into your WordPress site dashboard, navigate to Plugins → Add New, search for “Jetpack,” and click Install. After Jetpack has been installed, click Activate.
2. Connect Jetpack to your WordPress.com account
Go to Jetpack → My Jetpack in your website’s WordPress dashboard. Under Connection, click Connect. You will then be prompted to connect your user account.
Enter your WordPress.com credentials if you are not logged in already and click Connect your user account.
Next, click Approve to connect your site to WordPress.com.
3. Activating Jetpack Scan
In your site’s WordPress dashboard, go to Jetpack → Dashboard, then click on the My Plan tab. In the upper left of that tab is text that says, “Got a license key? Activate it here.” Click Activate it here.
From here, you can choose the license key associated with your purchase and click Activate.
Note: Once the site is connected to Jetpack Scan, your site will remain on the Jetpack Scan solution, even if you change or add a Jetpack plan or move your site to a new host.
Completing Jetpack Scan setup
As soon as Jetpack Scan is activated, the first scan begins immediately. However, there are a few more things you will want to do:
1. Make sure file permissions are set correctly
In order for Jetpack Scan to scan a website, it needs to be able to create files in the /Jetpack-temp/ directory (which is located in the root of the site alongside /wp-content/ and /wp-includes/). It writes a temporary helper file to this directory during the scan and removes it after the scan is complete.
If your site is hosted on a server that prevents files from being changed, you will need to work with your host to ensure that Jetpack can write files to the /Jetpack-temp/ directory.
2. Add server credentials
Jetpack can scan your site without any server credentials, but server credentials are required to use one-click fixes. The server credentials can also help make the scans faster and more reliable.
Read more on how to add remote access/server credentials.
Running a scan
Go to Jetpack → Scan in your site’s WordPress dashboard. After opening the Scan page, you will see two interfaces: Scanner and History.
The Scanner page provides an at-a-glance reference of the site’s current state. It will either show that the site is looking great or list any currently active threats.
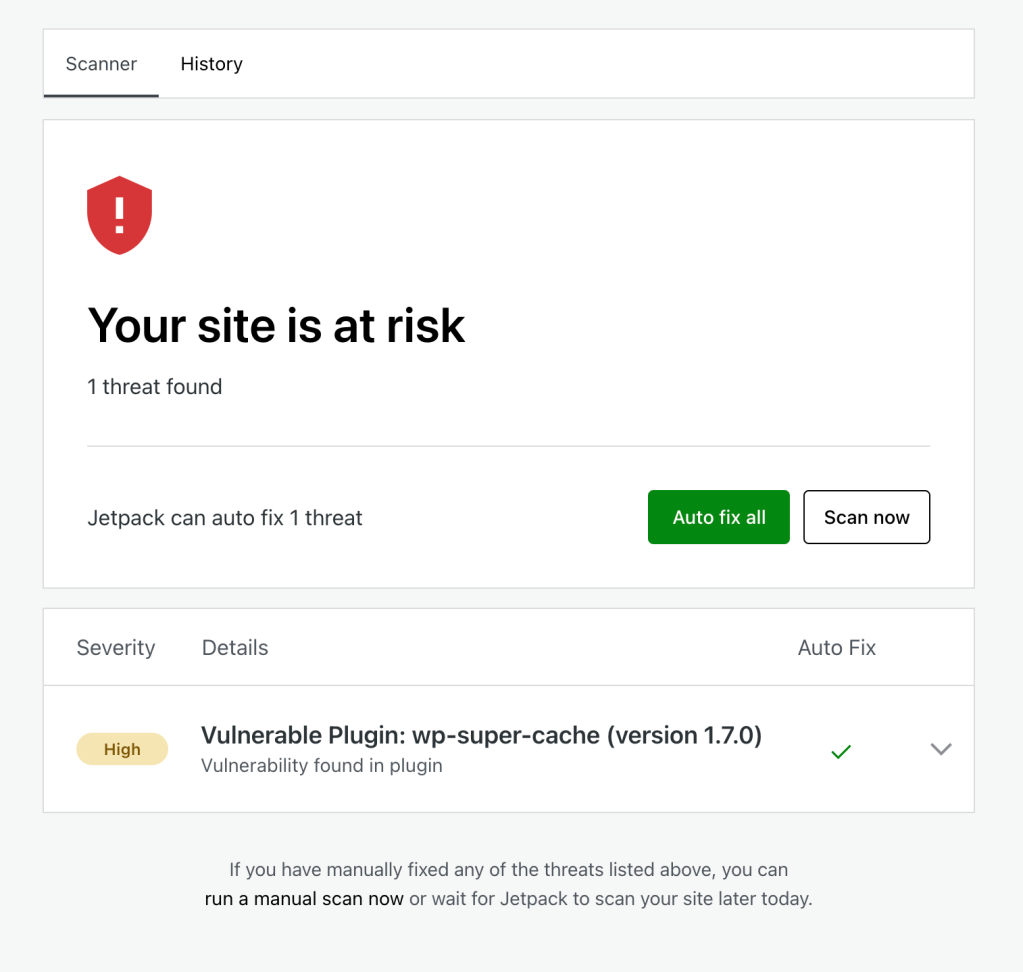
Clicking the Scan now button will start a new scan.
On the history page, you’ll see a list of all previous threats that affected your site. You can filter them by their fix/ignore status, and still decide to fix Ignored threats if you’d like.
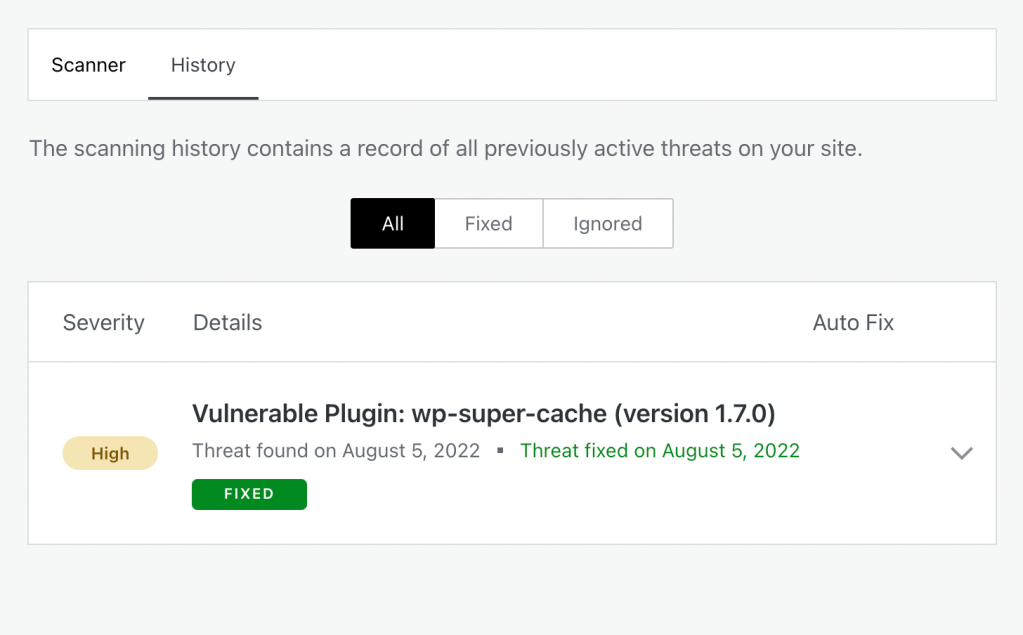
Once a scan completes, you will receive a notification if any threats are found. These notifications will be in your site’s WordPress admin, your WordPress.com dashboard, and sent to you via email.
What data is scanned?
- All files in the plugins, must-use plugins, themes, and uploads directories.
- Specific files from your WordPress root directory, like /wp-config.php.
- Other select files inside the /wp-content directory.
How often do scans occur?
Scans occur daily or when manually triggered.
How do I fix threats?
Jetpack Scan offers one-click fixes for most threats detected.
The Auto-fix all button will handle all the threats at once. If you want to address each threat individually, you can click on the threat to see more information about the problem. From here, you can click Ignore threat or Fix threat.
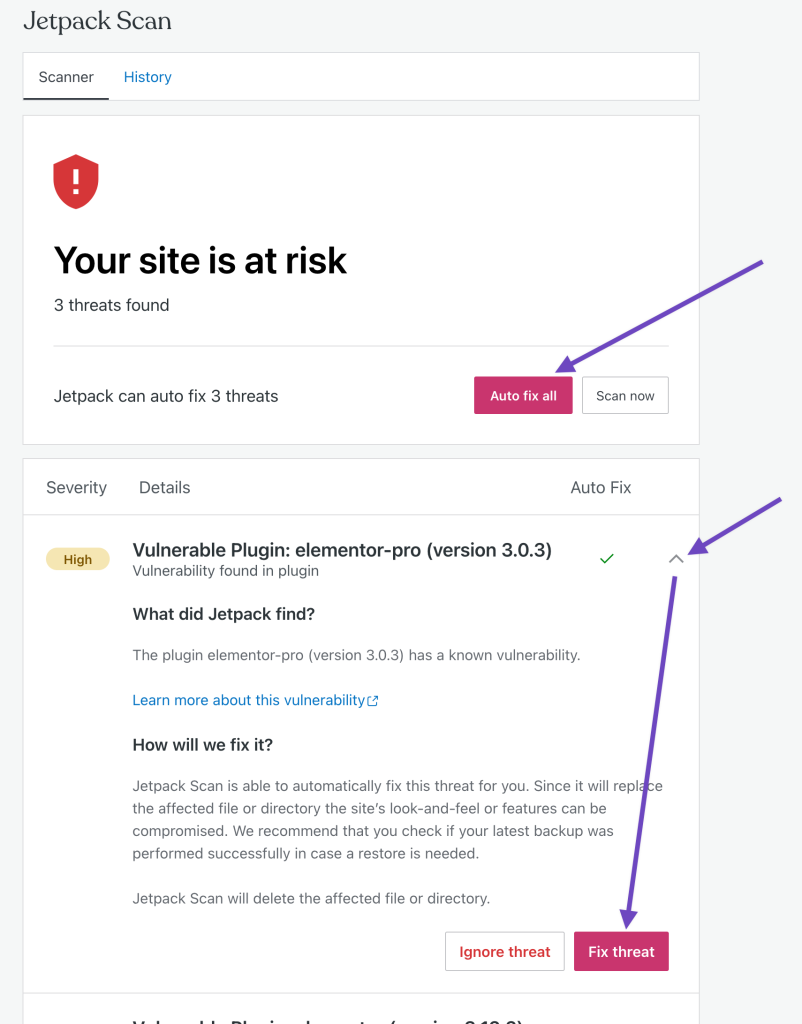
The threats and whether they have been ignored or fixed will be logged in the History tab.
For more complex issues that cannot be resolved with a one-click fix, follow this guide to cleaning a hacked WordPress site. It will lead you through removing malware and improving your site’s security to guard against future hacks.
Frequently asked questions
What exactly is malware, and how does it differ from other cyber threats?
Malware is a broad category of software that makes use of malicious code injection with the specific intent of harming, exploiting, or compromising computer systems, networks, and data. Malware encompasses a wide range of software types such as viruses, worms, Trojans, spyware, adware, ransomware, and rootkits.
One way that malware differs from some other threats is its intent. Malware is purposefully created to compromise, damage, steal, or manipulate data and gain unauthorized access to systems.
Malware also functions differently than other threats.
Some aspects of malware functionality include:
- Covert operation. Malware is designed to evade detection so that it can carry out its purpose uninterrupted.
- Propagation techniques. Malware spreads through a variety of means, including email attachments, infected files, malicious downloads, infected websites, removable media, and social engineering tactics.
Some types of malware, like viruses and worms, can self-replicate and spread to other systems autonomously, creating a cascade of infections.
- Payloads. Malware carries a payload, which is the malicious action it intends to execute. This can include stealing sensitive data, damaging files, conducting surveillance, or launching attacks on other systems.
- Command and control. Many malware variants establish a connection with remote servers controlled by cybercriminals, allowing them to receive instructions and updates, upload stolen data, or propagate to other targets.
- Evolution and adaptation. Malware continually evolves to evade detection and improve its effectiveness. Cybercriminals frequently release new versions and variants of malware to exploit emerging vulnerabilities.
In contrast, other threats may not always have malicious intent, have an automated mechanism to spread or deploy harmful code, or be designed to operate covertly. For example:
- Vulnerabilities and exploits. Vulnerabilities are weaknesses in software or systems that can be exploited by attackers. Exploits are tools or techniques that take advantage of these vulnerabilities. While exploits can lead to malicious actions and the installation of malware, exploits do not necessarily involve deploying malware.
- Security misconfigurations. Security misconfigurations result from mistakes in configuring software, servers, or networks. These errors can expose systems to attacks, but they are not created with malicious intent.
- Phishing and social engineering. Phishing attacks and social engineering may also include a malware component, but many such attacks simply rely on deception rather than malicious software. They trick individuals into revealing sensitive information or taking harmful actions by posing as a trusted source like a friend, family member, or service that you use.
- Denial-of-service (DoS) attacks. DoS attacks aim to disrupt services or networks by overwhelming them with excessive traffic or requests. While the impact can be harmful, DoS attacks don’t involve malware or unauthorized access.
- Brute force attacks. Brute force attacks involve attempting every possible combination of passwords or encryption keys to gain access to a system. While they can lead to unauthorized access, they don’t necessarily involve malware.
While malware is explicitly created to carry out harmful actions, other threats may involve vulnerabilities, exploits, misconfigurations, or social engineering tactics that can also compromise systems but without the use of any specific harmful software. Each type of threat requires specific prevention and mitigation strategies to protect against its potential consequences.
How do hackers commonly introduce malware into a WordPress website?
Hackers can use vulnerabilities in plugins, themes, and WordPress core files to install malware on WordPress sites. They can also take advantage of security misconfigurations, use phishing techniques or social engineering, and brute force attacks to gain unauthorized access and install malware on your site.
One common method is gaining admin access by trying common usernames like “admin” along with a database of leaked passwords, which is why unique usernames and longer more complex passwords are important for security.
The malware they introduce can take a variety of forms including:
- Viruses. Viruses are designed to replicate themselves and spread from one system to another. It attaches or embeds itself into legitimate programs or files, and when these infected programs or files are executed, the virus code activates and can infect other files and systems.
- Worms. Worms are similar to viruses in that they are designed to self-replicate. The difference between worms and viruses is that viruses attach themselves to existing files and rely on user actions to propagate. Worms are self-contained programs and can spread automatically.
- Trojans. Trojan malware, named after the famous Trojan Horse in Virgil’s Aeneid, often disguise themselves as harmless or desirable software or other file types, tricking users into downloading and executing them. Trojans use a variety of methods to steal sensitive data, damage files, download additional malware, or spy on user behavior.
- Spyware. Spyware is designed to covertly gather information without the user’s knowledge or consent. The information could be personal data, browsing habits, or keystrokes to capture login credentials and credit card information.
- Ransomware. Ransomware encrypts a victim’s files or locks them out of their accounts or devices, making them inaccessible. The attacker then demands a ransom, typically in cryptocurrency like Bitcoin, from the victim to provide the decryption key or unlock the compromised system. Ransomware attacks are financially motivated and have become increasingly prevalent in recent years.
- Rootkits and backdoors. Rootkits and backdoors attempt to gain unauthorized access and control over a website, network, or device by creating admin-level access that bypasses normal authentication protocols. Rootkits and backdoors are particularly stealthy and sophisticated, as they are often used to maintain persistent and hidden access to a compromised system while evading detection by security software and administrators.
If my WordPress site is small, am I still at risk of malware attacks?
Every website, no matter how big or how small, is at risk of attempted malware attacks. In fact, many small to medium-sized websites are at a greater risk of attack because hackers know that these types of sites generally have less knowledge about and fewer resources to dedicate to security.
Does Jetpack Scan offer real-time malware scanning?
Jetpack’s WAF runs in real time, but the malware scan runs on your site automatically each day. You can also manually scan your site at any time.
Can malware scanners slow down my website’s performance?
Local malware scanners, which use your server’s resources to scan your site, can slow down your site’s performance. Remote scanners that use off-site servers to perform scans do not impact your site’s performance.
Are there different types of malware scanners and, if so, which is the best for WordPress?
Yes, there are different types of malware scanners — local scanners, fully remote scanners, and remote scanners that have local server access via a plugin.
Local scanners can perform deep scans on your files and directories, but the information that is being used to compare your website against is stored on your server, which makes it vulnerable to tampering by malware. Because the local scanners use server resources to run their scans, they can also affect website performance, so you’ll want to schedule scans at times when traffic is lower on your website.
Purely remote scanners, like browser-based scanners that you type your website URL into and then manually run a scan, can only scan publicly available directories and pages on your website. This means that they can’t detect malware that is hidden at a deeper level. They do, however, run on their own servers, which helps maximize site performance during scans.
Among these types of scanners you’ll also find some functionality differences. For instance, some scanners must be manually operated while others can be set to automatically scan your website at periodic intervals (daily, weekly, monthly, etc.). Scanners can also differ in the quality of scans they perform and the methods they use to scan your WordPress site.
The best scanner type for WordPress sites is one like Jetpack Scan that uses remote scanning but also has access to all your files and directories so that it can run thorough, automated scans that don’t impact website performance. It should also log scan history and activity data and store it on a remote server so you’ll be able to access them even if your website goes down, or you are locked out of your website.
How often should I run malware scans on my WordPress site?
It’s advisable to scan WordPress sites on a regular schedule, even if you don’t suspect an infection. The frequency depends on your website’s activity, how often you update or add content, and the level of risk you’re comfortable with. For active websites, daily or weekly scans are often recommended.
Here are some other times you might want to run a malware scan:
- After suspicious activity. Whenever you notice anything unusual on your website — such as unexpected pop-ups, slowdowns, unauthorized access, spam emails originating from your website, or suspicious files — it’s essential to run a malware scan immediately. Quick action can prevent further damage or data loss.
- After installing new plugins or themes. After installing any new plugin or theme, especially from untrusted sources or unfamiliar websites, consider running a malware scan on those files before activating them. This practice helps ensure the safety of newly acquired content.
- After plugin and theme updates. It’s a good practice to run a malware scan after performing any updates to make sure that nothing has been compromised.
Remember that while regular scans are important, prevention is equally crucial. Implement strong security practices, update all software, use reputable security tools with real-time firewall protection, and exercise caution when downloading files or clicking on links. Combining these practices with periodic malware scans helps maintain a secure and reliable website.
Do malware scanners also remove the detected threats, or do they just identify them?
Some malware scanners can remove malware for you. For example, Jetpack Scan offers one-click fixes for malware removal. Other scanners only identify security threats or may require that you upgrade to a higher tier of service to enable automated malware removal.
Some malware is too complex to be removed automatically. In such instances, you should follow this guide to detect and remove malware from a WordPress site.
In addition to scanning, what other security measures should I adopt for my WordPress site?
Malware scanning is just one component of a good security strategy. There are other things you should do to help keep your WordPress site safe. Below are some best practices for website security that you should consider implementing:
- Keep WordPress core, themes, and plugins updated. Regularly update your WordPress core software, themes, and plugins to the latest version. Outdated software can sometimes have vulnerabilities that attackers can exploit. Reputable developers keep on top of security loopholes in their software and release updates to eliminate them. Keeping your website’s software up-to-date will minimize the number of weak points in your site’s software and infrastructure.
- Use strong authentication. Avoid using the default “admin” username for your administrator account and don’t use the same username as your display name. Implement strong and unique passwords for your WordPress user accounts. Enable two-factor authentication (2FA) for an additional layer of login security.
- Limit login attempts. Limit the number of login attempts to prevent brute force attacks. Jetpack Security automatically limits login attempts as part of its brute force protection features.
- Take regular backups of your site. Automate regular backups of your website and its database and, if you don’t have real-time backups, take a manual backup of your website before you make any major changes like updating, adding, or removing plugins. Ensure that backups are stored securely and remotely so that you can access them even if your website becomes unavailable due to a malware infection or some other reason.
- Choose a secure host. Host your website with a reputable hosting provider that specializes in WordPress security. Ensure that the server and hosting environment are configured securely.
- Use firewall protection. Implement a web application firewall (WAF) to filter out malicious traffic and block common security threats.
- Set secure file permissions. Set WordPress directory and folder permissions to 755. File permissions should usually be set to 644, except for wp-config.php, which should be set to 600.
- Disable directory listing. Prevent your website’s directory from being listed publicly by configuring your web server to hide directory contents.
- Security headers. Implement HTTP headers like content security policy (CSP), X-Content-Type-Options, and X-Frame-Options to enhance your site’s security.
- Use HTTPS encryption. Most browsers require that websites have a secure HTTPS connection and valid SSL certificate in order to display correctly. If your site uses http:// in front of its URL instead of https://, it may be marked as insecure and browsers may display a warning that your site is unsafe. Many hosting providers offer free SSL certificates to make this process seamless.
- Improve your database security. Change the default database table prefix from “wp_” to something unique like “xyzzy_” during WordPress installation to thwart SQL injection attacks.
- Restrict user permissions. Limit user permissions to the minimum necessary for each role. Avoid assigning admin-level access to users who don’t need it.
- Monitor file changes. Set up file change monitoring to receive alerts when critical files are modified or added unexpectedly.
- DDoS protection. Consider a DDoS protection service or CDN to mitigate distributed denial-of-service attacks. Jetpack Complete offers both DDoS protection and a CDN, among other features.
- Security hardening. Implement security hardening measures by disabling unnecessary features and services, such as XML-RPC, pingbacks, and trackbacks.
- Invest in educating users. Train your team on security best practices to prevent social engineering and phishing attacks. In registration forms and account management areas of your website, explain clearly and concisely your security requirements and why they are necessary in a way that doesn’t overwhelm or annoy your users.
- Develop an emergency response plan. Develop a plan for responding to security incidents. Know how to quickly restore your site from backups if needed.
Remember that security is an ongoing process, and it’s essential to stay vigilant and keep your WordPress website updated and protected against evolving security threats. Regularly review your security measures and adapt them as needed to maintain a secure online presence.
To streamline your security process, use a security plan, like Jetpack Security, that will automatically scan your website and that offers broad threat prevention and detection features.
To learn more about steps you can take to secure your WordPress site, consider reading the following articles: WordPress Security: How to Secure Your Site from Hackers and How to Find, Access, and Edit wp-config.php in WordPress.
Jetpack Security: Automated malware scans, one-click fixes, and backups for WordPress
Your website is one of the key places where trust in your brand is built. It’s where you interact with readers, convert new subscribers, and store the data of customers. If your website isn’t well-guarded against attacks, it can critically damage your business and compromise your users’ information.
Using a best-in-class WordPress security plugin that offers a layered approach to security is crucial to protecting your users, yourself, and your brand.
Jetpack Security is developed and maintained by the people behind WordPress.com, so it’s designed specifically for WordPress by developers with in-depth knowledge of WordPress security. Jetpack Security features include:
- Comment and form spam protection
- Real-time cloud backups
- 10GB of backup storage
- A 30-day archive and activity log
- One-click restores
- A website firewall
- Automated daily malware and vulnerability scanning
- One-click fixes for most malware issues
- Instant email threat notifications
- Single Sign-on (SSO) and 2FA integration for login security
- Priority support
Jetpack Security also takes advantage of remote scanning techniques, so there’s no impact on your website’s speed and performance. Backups and activity logs are hosted off-site so you always have access to them even if your website goes down.
If your site does go down or Jetpack’s connection to your site is lost, you’ll get an immediate email notification (or upgrade to Jetpack Manage and opt in to SMS text alerts) so that you can respond as quickly as possible to any issues or security threats.
Get Jetpack Security today and enjoy peace of mind and top-tier protection for your website.
We guard your site. You run your business.
Jetpack Security provides easy‑to‑use, comprehensive WordPress site security, including real‑time backups, a web application firewall, malware scanning, and spam protection.
Secure your site