A SQL injection (SQLi) is when hackers insert harmful code into a database in order to access sensitive information like personal details or credit card data. Unfortunately, this is one of the most common threats on the web. So if you’re a website owner, you’ll want to familiarize yourself with SQL injection prevention.
Once you learn about the different types of SQLi attacks and their common targets, you’ll be better equipped to protect your site against them. You might decide to implement input validation, deploy a web application firewall, or run a vulnerability scanner.
In this post, we’ll discuss everything you need to know about SQL injection in cybersecurity. We’ll start by answering, “What is SQL injection?”, and other questions about the most common types of attacks and targets. Then, we’ll look at some of the potential risks and impacts of SQLi attacks. Finally, we’ll show you how to prevent SQL injection.
What is a SQL injection?
To understand the basics of this common cyberattack, you’ll first need to have some knowledge of Structured Query Language (SQL). This is a programming language used in web applications and databases. It enables you to access, manage, and manipulate structured or relational data. SQL data tables consist of simple columns and rows.
You can use SQL queries or “commands” to change, add, or delete information. Alternatively, you can simply extract data sets for analysis.
Let’s say you have a SQL database of instructor salaries and want to get a broad sense of how these earnings compare. In that case, you might use this SQL query:
SELECT Id, Name, Salary,
(SELECT Count(*) from instructor ii where ii.salary > i.salary) as num
from instructor i;This asks your database to return each instructor’s name, their salary, and a number value indicating how many people make more than the specific professor listed.
A SQL injection occurs when a hacker inserts malicious code into your application or database to interfere with it. In many cases, the aim is to access hidden information or bypass authentication mechanisms.
Hackers may then be able to change or delete the information in your data tables. More severe SQL injection attacks can damage your website’s underlying server or infrastructure. If an attacker overloads your database with excessive SQL queries, this is a variation of a distributed denial of service (DDoS) attack.
The different types of SQL injection attacks
There are three different types of SQL injection attacks. Let’s take a close look at them.
In-band SQLi
In-band SQLi attacks (also referred to as “classic” SQLi) are typically the easiest to detect and exploit. In this scenario, the hacker only uses one communication channel to get a direct response.
In other words, they use the same medium to launch the attack and retrieve the results. One common example of this would be an attack executed on a web page.
The two main variations of in-band SQLi are:
- Error-based SQL injection attacks. This is when hackers insert malicious queries into a database to intentionally trigger an error message. When this happens, the resulting error message reveals sensitive information which can enable them to carry out further attacks and enumerate the database.
- Union-based SQL injection attacks. In this case, the attacker uses the UNION operator to pull data from more than one table. The results will show at least one legitimate data set while also revealing a data table that should be hidden.
As we mentioned, these are some of the most common types of SQLi attacks.
Blind SQLi
Another, more sophisticated and covert form of SQL injection is the blind SQLi attack. It’s also called an “inferential SQLi”.
With this type of cyber assault, the hacker inserts malicious code into the web application, but can’t see the results directly (as with classic SQLi). That means they are working “blindly”, hence the name.
In order to expose the desired data, hackers can then send SQL queries that reveal sensitive information based on time delays or Boolean behavior.
With time-based blind SQLi, the malicious query forces the database to wait a specified amount of time before it can respond. Hackers can then infer whether the response is TRUE or FALSE based on the time delay.
Meanwhile, with boolean or content-based SQLi attacks, the query forces the database to return different results. Those results allow the hacker to infer whether the content is true or false.
Blind SQLi attacks typically require many iterations in order to retrieve enough information to enumerate the database. For this reason, they are typically slower and more difficult to execute.
But the advantage (for hackers) is that due to their subtlety, blind SQLi attacks can go undetected for longer periods of time. As a result, the cyber perpetrators may be able to extract more valuable data (and wreak more havoc) than they would with a classic SQLi attack.
It’s also worth noting that bot-driven SQLi attacks can be especially dangerous, as they enable hackers to work much faster.
Out-of-band SQLi
The last type of SQL injection attack is out-of-band SQLi. Unlike an in-bound SQL injection, this variation requires multiple communication channels to carry out the attack.
Typically, out-of-band SQLi only works for servers that can trigger HTTPS or DNS responses (which is the case for most SQL databases). One common example of out-of-band SQLi is when hackers insert code that triggers the server to intercept users’ login credentials, sending them to a remote endpoint.
Common SQL injection targets
Now that we’ve gone over the main forms of SQL injection, let’s go over the most common targets for these types of attacks.
1. Content management systems (CMS)
A content management system (CMS) enables users to create, modify, and manage web content. Some examples include Wix, Joomla, and WordPress.
These solutions are more sophisticated and customizable than website builders like Squarespace. You can use a CMS like WordPress to build almost every kind of website, from a simple portfolio to a thriving online store.
That said, many CMSs use the MySQL database system to manage content. By design, this makes them a target for SQL injection attacks.
What’s more, some CMSs like WordPress are open source. This means that the software is free to download and anyone can alter it. In the case of WordPress, the CMS also receives regular maintenance and security updates, which include important vulnerability patches.
Since the contents of these updates are made public online, hackers can study them to learn how to exploit them. Then, they can target websites that are running on older, less secure versions of WordPress.
On top of that, websites built with CMSs typically include engagement features like contact forms, search bars, and comment sections, which can be vulnerable points for SQL injection attacks.
2. Third-party plugins and integrations
Many CMSs and other website building tools rely on third-party plugins to expand their functionality. For instance, WordPress has a vast plugin directory of nearly 60,000 tools.
You can use these plugins to add everything from security solutions like Akismet to performance optimization tools like Jetpack Boost.
Integrations work similarly to plugins and extensions. For instance, many popular marketing solutions, like Mailchimp, offer integrations (which are often facilitated using plugins or extensions).
Basically, plugins and integrations enable users to create a highly custom website. But the developers of the core WordPress software aren’t controlling all the free and premium plugins on the market. Therefore, the integrity and security of every single tool isn’t regulated. It’s up to website owners to ensure that they’re installing high-quality plugins. One way to do this is by selecting plugins from the WordPress.org library.
It’s also up to website owners to make sure that all plugins are up-to-date. If they aren’t, hackers can use vulnerability databases to exploit outdated software (more on this later).
3. Data-intensive applications
As we’ve discussed, SQL is a programming language used in database management systems, and SQL injections target these databases to extract, modify, add, or delete data with nefarious intent.
Naturally, data-intensive applications become the most viable targets for this type of cyber assault. Hackers have the most to gain when there are large amounts of data to be extracted.
Therefore, online stores and large websites are likely at a higher risk of SQLi attacks.
4. Legacy code and outdated systems
As we mentioned, outdated software and systems can increase a website’s chance of becoming hacked via SQL injections. This is especially true when a site is built on open-source software like WordPress, Drupal, or Joomla.
That’s because cyberattackers can utilize databases or public records of security patches to find and exploit these vulnerabilities. Legacy code can also be a big problem with older websites.
5. Data APIs and web services
As we discussed, many websites built on CMSs use a variety of plugin integrations to streamline the website management process. Most of these integrations work thanks to data application programming interfaces (APIs) that utilize SQL.
For example, the WordPress REST API enables the CMS to communicate with all the necessary applications.
Similarly, Drupal and Joomla have their own proprietary APIs. These APIs can allow for the use of free or premium extensions as well as other web services like analytics or security software.
Since APIs are constantly processing requests, there are many opportunities to exploit SQLi vulnerabilities.
Motivations behind SQL Injection attacks
So far, we’ve explained in detail what SQL injection entails, but you may still be wondering about the motivations behind these attacks.
Here are some of the most common intentions:
- Data theft and manipulation. Many SQLi attacks aim to steal data or manipulate the database into carrying out requests to its detriment. Stolen data can then be used to commit other cybercrimes like ecommerce fraud or identity theft.
- Malware and ransomware distribution. Some SQL injection assaults attempt to compromise a website’s database, infrastructure, or server using malware. They may want to take down a website or gain access to the root server (and thereby the database content).
- Impact on website integrity and reputation. A more covert motivation for SQLi attacks is to damage a company’s reputation. For instance, hackers who dislike your business may steal and expose customer data to send a message.
Of course, it’s important to understand the motivations behind these cyberattacks, but being aware of the impact of malicious SQL injections is also crucial. We’ll dive into this in the next section.
The impact of SQL injection attacks
We’ll start with the less serious consequences for your website visitors. These are mostly inconveniences which can lead to a poor user experience.
Essentially, when SQLi attackers modify your data tables, it can lead to ongoing issues that interfere with the operations of your web pages, online forms, and more. This negative outcome shouldn’t be downplayed, as your visitors expect to use your website without issues. Running into difficulties can cause them to leave your website.
When it comes to businesses and organizations, the impact can be more severe. In particular, online stores tend to hold a lot of sensitive customer information, like physical addresses for shipping and credit card numbers for payments.
If an SQLi attack leads to a data breach, your clients’ personal information can be sold to scammers. This could put them at risk of phishing schemes, identity theft, credit card fraud, and more. It may also damage your business’s reputation or lead to monetary losses.
Furthermore, failing to protect sensitive user information can translate to non-compliance with certain online security standards or data protection laws like the PCI-DSS and the GDPR.
This can put companies at a greater risk of litigation in the case of a data breach. Of course, the risks become higher if your online business is in a regulated industry like healthcare or finances, as such companies are subject to higher standards for data privacy and protection. For instance, medical practices will need to remain HIPAA-compliant.
How to prevent SQL injection attacks
Now that you know about the potential impacts of SQL injection, we’re going to show you how to prevent SQL injection. We’ll go over seven different strategies that you can implement.
1. Implement input validation
One of the best SQL injection prevention strategies is to implement input validation. This can help ensure that only legitimate users are interacting with your database — and in an appropriate manner.
There are plenty of powerful data validation techniques that you can use with SQL. For starters, you could try built-in SQL constraints like UNIQUE or NOT NULL.
Additionally, you might want to use data and display types to define how information is stored and presented. You can also use regular expressions (RegEx) to define what data patterns are acceptable.
With any of these strategies, SQLi attackers will be stopped in their tracks since their nefarious inputs will be flagged as invalid.
2. Regularly update your software and database
As discussed, various types of outdated software can become targets for SQLi attackers, especially if you’re using open-source software. Therefore, one of the easiest ways to prevent SQL injection attacks is to regularly update your software and database. This process will depend on what CMS or website builder you use.
With WordPress, updating the core software is simple. Go to Dashboard → Updates.
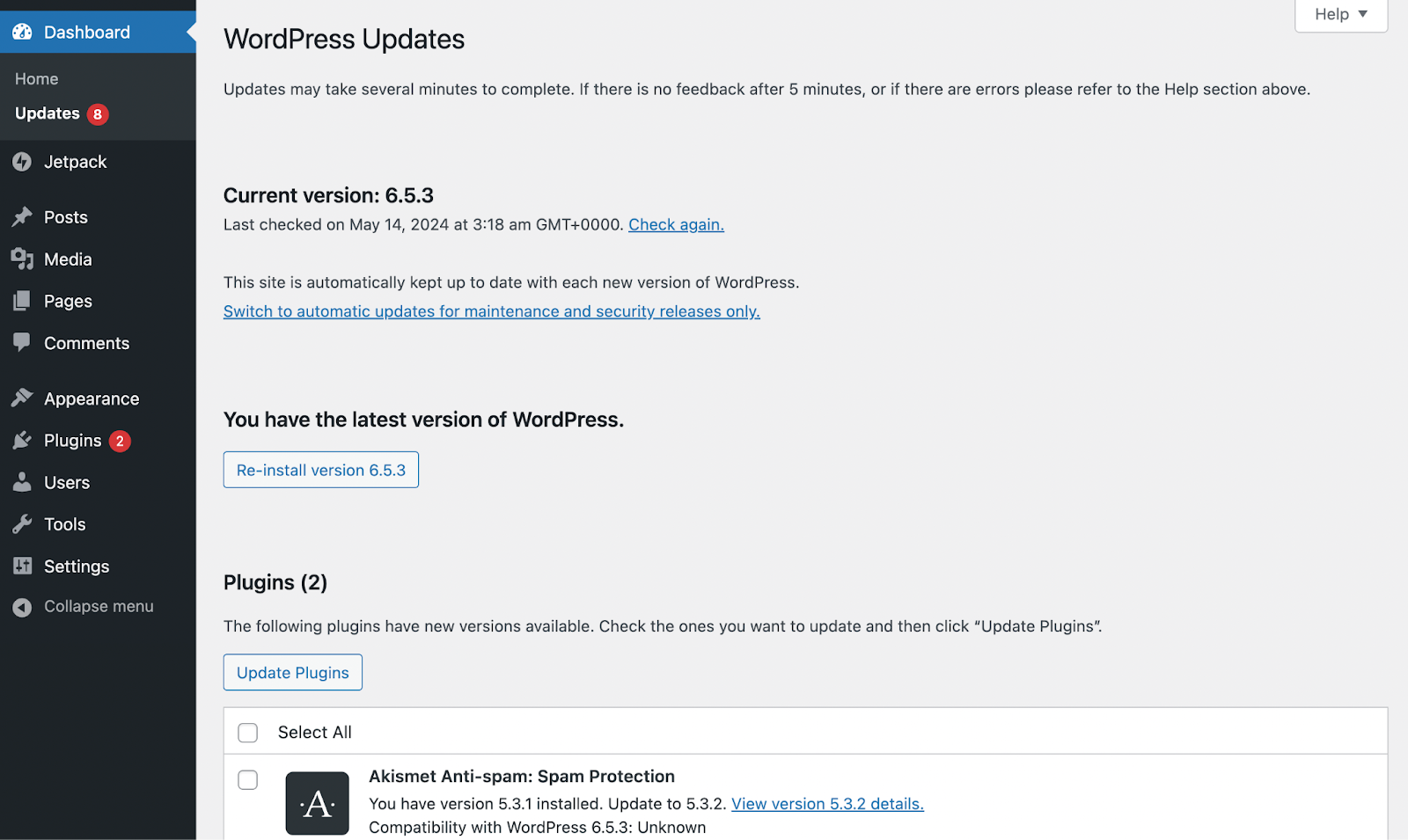
You’ll see a red notification when you have any available updates, but you can still check these at any time. At the top, you can update WordPress. Scroll down to update any plugins or themes.
Before you update any software, it’s important to make a backup of your website. Updates can lead to unforeseen issues on your site, especially if you’ve installed a lot of plugins.
You can’t anticipate how updated software will interact with other tools on your site. Therefore, as a general rule, you’ll want to avoid installing too many WordPress plugins.
Ideally, you’ll create automatic backups so you don’t lose important data. Alternatively, you might want to use a staging site to test updates before you make them live.
Updating your database can be more involved. Again, this will depend on the platform you’re using.
With WordPress, there are several ways to clean and optimize your database. If you’re a more experienced user, you might want to update your database using phpMyAdmin.
Installing a plugin like Jetpack Akismet Anti-Spam can also help keep your database in an optimal state.
That’s because it minimizes the number of spammy comments and form submissions you receive. This can even block SQLi attacks based on suspicious behavior.
We guard your site. You run your business.
Jetpack Security provides easy‑to‑use, comprehensive WordPress site security, including real‑time backups, a web application firewall, malware scanning, and spam protection.
Secure your site3. Implement role-based access control (RBAC)
Larger websites tend to have a lot of people collaborating on the back end. For instance, an ecommerce site with a blog might have a developer, web designer, shop manager, marketing specialist, and various blog writers.
If these users are given too many permissions, they can accidentally create security vulnerabilities on your site — including those that lead to SQLi attacks.
Therefore, you’ll want to implement role-based access control (RBAC). When you do this, consider the principle of least privilege, which is a good practice in cybersecurity.
With this approach, you’ll give each user the minimum permissions necessary to perform their tasks. As an example, a blog writer for a clothing website should only be able to create posts, and not access other more delicate parts of the website, like the product catalog.
With WordPress, you can easily assign all users a role. To do this, go to Users → All Users. Then, find the user in question and click on Edit.
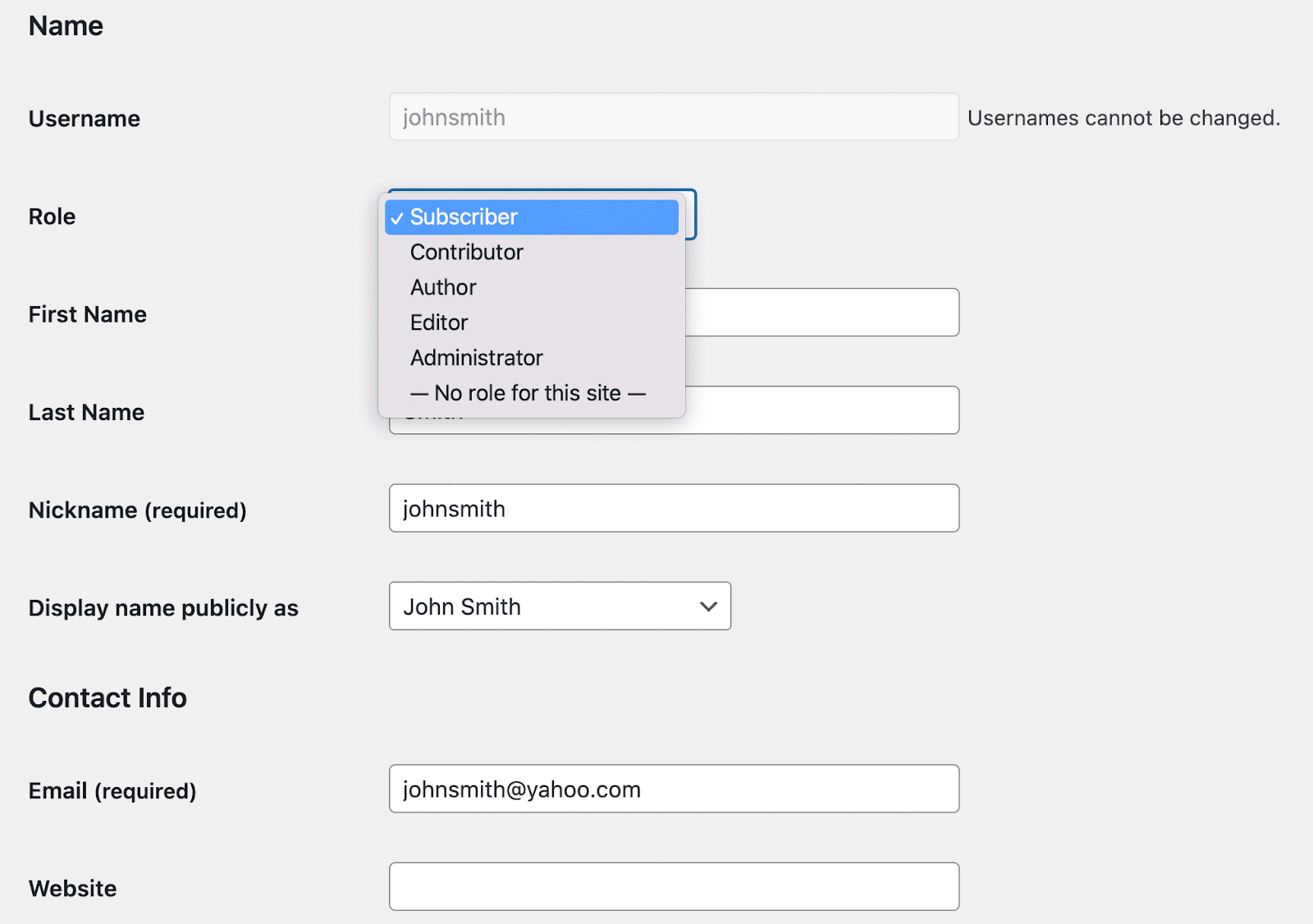
In the Role dropdown menu, you’ll be able to choose the most appropriate role for that person. There are five WordPress user roles by default, but you’ll get more when you install certain plugins like WooCommerce.
4. Deploy a web application firewall (WAF)
A web application firewall (WAF) is another excellent defense against SQL injection attacks. This is software that sits between client applications and web servers, and filters all traffic (both incoming and outgoing).
A WAF searches for suspicious activity and requests, blocking them when necessary. This security solution is ideal for SQL injection prevention because some attacks are easy for a WAF to spot.
Additionally, some WAFs let you set rules for IP addresses. You can create allowlists and blocklists to control who can access your site.
Some managed hosting providers will install and manage a WAF for you. Otherwise, you may need to purchase your own firewall. Jetpack Scan is a powerful solution for WordPress websites and also offers automated malware scanning.
5. Run a vulnerability scanner
A vulnerability scanner can help safeguard your site against many common threats, including SQLi attacks. It simply inspects your site regularly and compares its findings against a database of known vulnerabilities.
For WordPress websites, the penultimate database is WPScan.
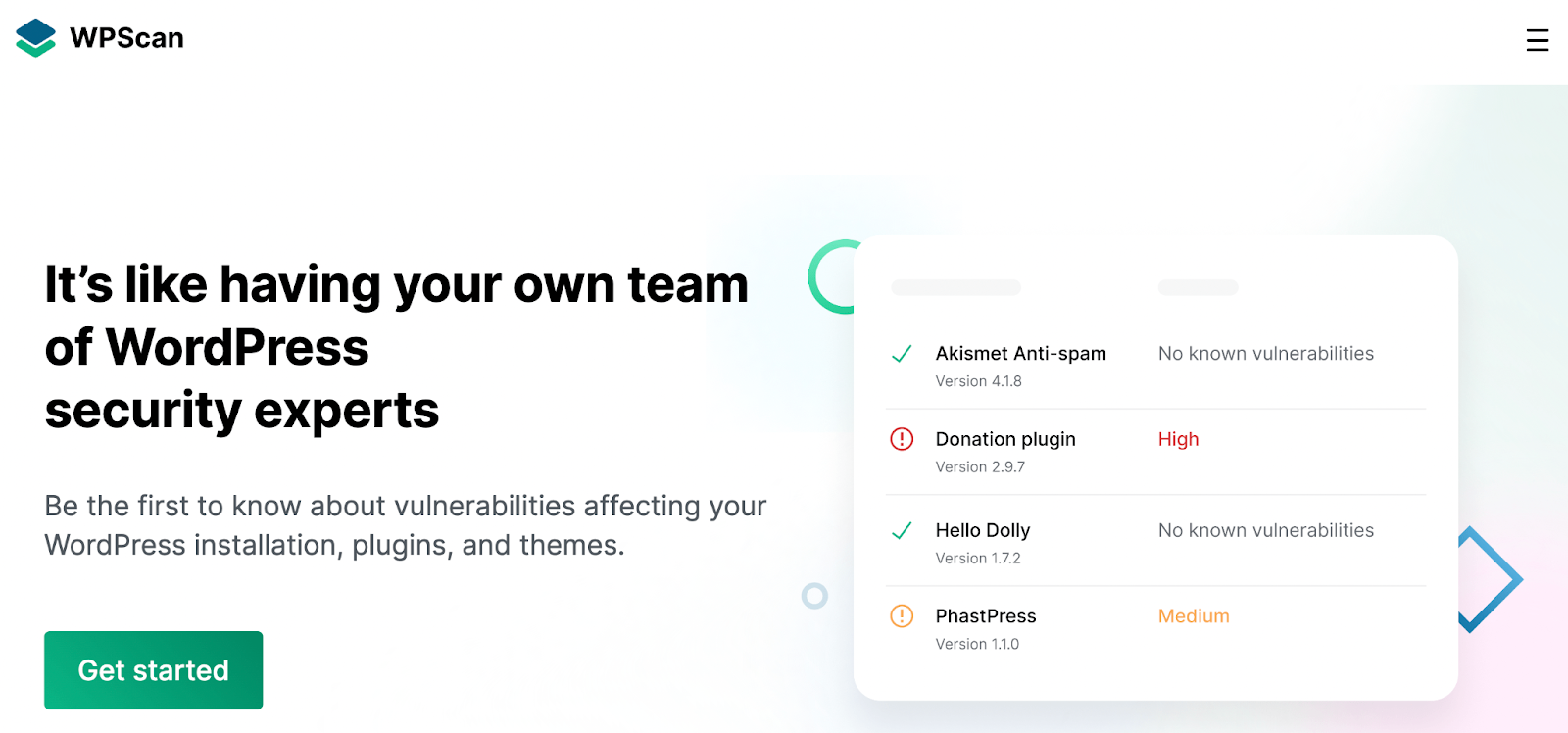
With over 50,000 vulnerabilities documented, this is one of the largest vulnerability databases. You can get access to this vital information when you install Jetpack Protect.
6. Conduct penetration testing
In cybersecurity, penetration testing (or simply “pentesting”) refers to a simulated cyberattack that’s meant to reveal vulnerabilities. This is also called “ethical hacking” and can be another excellent way to prevent SQL injection attacks.
With comprehensive penetration testing, web security experts analyze as much of your website as possible. This can include its systems, networks, core software, plugins, etc.
Once a pentester has identified vulnerabilities, they’ll attempt to exploit them (usually on a staging site). This way, they can more effectively assess risk and advise on eliminating these vulnerabilities.
This strategy involves hiring web security experts, so it could be costly. But if you own a large website or online store, pentesting can help protect your data.
7. Install an all-in-one security plugin
If you want to protect your website against SQLi attacks in a highly-efficient manner, you might consider using an all-in-one security plugin. This will typically include a vast suite of security features, including many of the tools we’ve discussed so far.
For instance, it might offer a WAF, vulnerability scanner, anti-spam software, and automatic backups.
Jetpack Security comes with everything you need for SQL injection prevention in WordPress. We’ll dive more into these security features in the next section.
How Jetpack Security helps prevent SQL Injections on WordPress
If you’re a WordPress website owner, Jetpack Security is one of the best solutions for preventing SQL injection attacks. It includes multiple WordPress security plugins: Jetpack VaultPress Backup, Jetpack Scan, and Akismet Anti-Spam.
That means Jetpack Security provides nearly all the SQL injection prevention features discussed in this article. These include:
- A web application firewall
- A robust vulnerability scanner
- An automated malware scanner
- Anti-spam software (to block comment spam and malicious form spam)
On top of that, you’ll get a complete backup solution, which gives you automatic backups in real time.
With VaultPress Backup, you won’t have to worry about creating a copy of your site when conducting routine updates and maintenance because you’ll always have a copy of your site on demand.
How to install Jetpack Security
Here’s how to install Jetpack Security in WordPress. To get started, navigate to your WordPress dashboard. Go to Plugins → Add New Plugin and search for “Jetpack”.
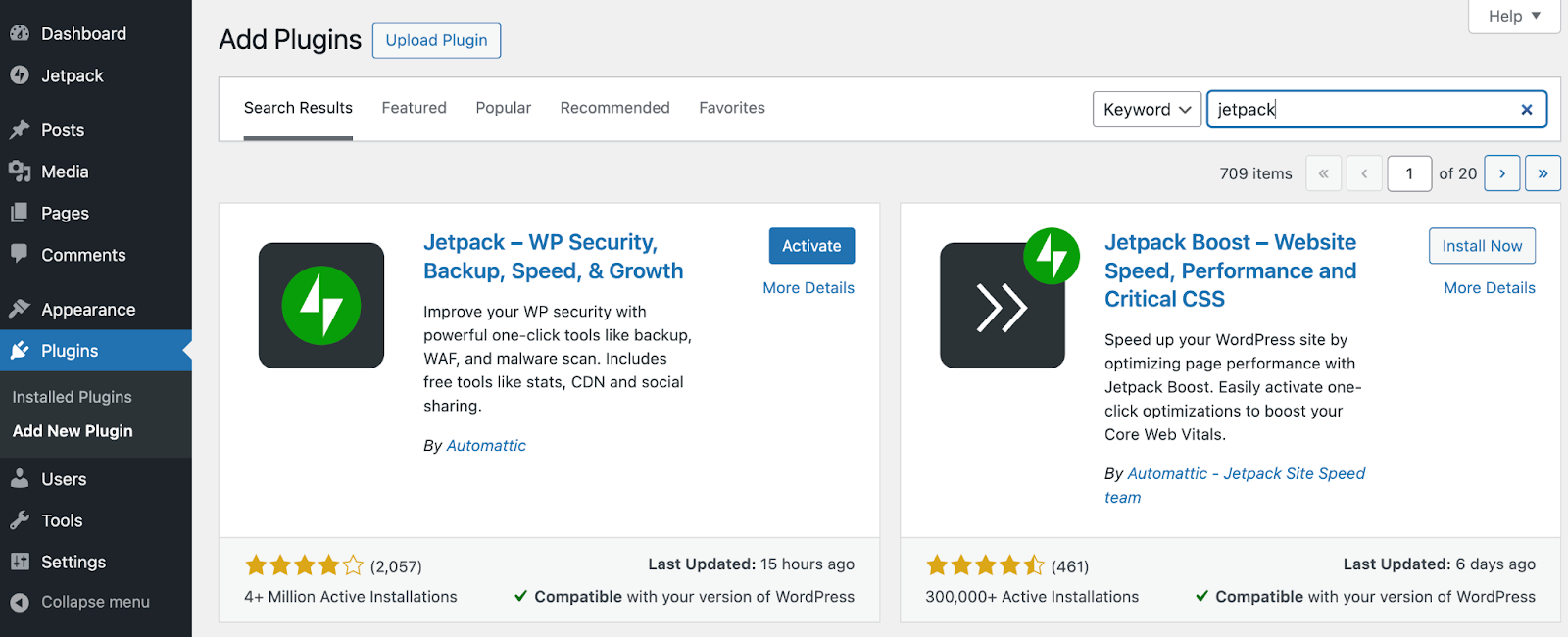
Click on Install Now followed by Activate. Then, you’ll be prompted to set up Jetpack. If you don’t already have a WordPress.com account, you’ll need to create one and connect it to your site.
After that, you’ll need to select the Jetpack Security plan and complete your purchase. It’s as simple as that!
You’ll then be able to configure your WAF, run your first vulnerability scan, and more. For more details on setting up Jetpack, check out our guide on how to get started.
Frequently asked questions
By now, we’ve covered a lot about SQL injection in cybersecurity. To wrap things up, we’ll review some of the most frequently asked questions on the topic.
What is SQL?
SQL is a programming language that’s popular in web applications and databases. It enables you to access, manage, and manipulate structured or relational data. SQL data tables consist of simple columns and rows.
What are SQL queries?
SQL queries, also called “statements” or “commands”, enable you to manage data. You can use them to add, delete, or modify information. Or, you can use them to extract data sets. Some of the most common SQL queries are SELECT, DELETE, UPDATE, DROP TABLE, and INSERT INTO.
What is SQL injection, and how does it work?
A SQL injection happens when a hacker inserts malicious code into a web application or database. Often, the goal of a SQLi attack is to access sensitive information or bypass authentication measures.
SQLi hackers may also try to change or delete the information in data tables and wreak havoc on your website’s operations. More severe SQL injection attacks can damage your web server or infrastructure. An attacker can also overload your database with SQL queries to conduct a DDoS attack.
What are the most common signs of a SQL injection attack?
Since SQL injection attacks use malicious queries to hack your site, the biggest indicator is a large volume of unusual queries to your database.
Similarly, if you notice that your web application is behaving unusually, this might also be a sign that SQLi attackers have tampered with it. You may also receive requests for database access, notice unexpected changes to your data, or find that certain users have been given more privileges than they should have.
How can I tell if my website is vulnerable to SQL injections?
Any website that uses SQL is vulnerable to a SQL injection attack. The risk becomes higher if you’re using a CMS, third-party tools and plugins, legacy code and outdated systems, data-intensive apps, or data APIs.
What role do web application firewalls (WAFs) play in defending against SQLi attacks?
WAFs filter all incoming and outgoing traffic. So, in many cases, they can quickly identify and block suspicious requests, thereby stopping SQLi attacks in their tracks.
When you use a premium WAF, like the one that comes with Jetpack Security, you can also create an allowlist. This way, you can decide which IP addresses are allowed to interact with your site.
Alternatively, you can create blocklists that prevent known hackers from attempting to attack your site.
How can I ensure that my plugins are not introducing SQL injection vulnerabilities?
The best way to ensure that your installed plugins aren’t opening your site up to potential SQLi attacks is to use a vulnerability scanner like the one offered in Jetpack Security.
Jetpack Security: Safeguard your WordPress site from SQL injections
SQL injection attacks occur when hackers compromise your database using malicious queries. They can lead to data breaches and put your personal information at risk. For online businesses, this can translate to a damaged reputation and revenue loss. Meanwhile, it can damage the user experience and expose your customers to online scams like phishing.
The good news is that there are plenty of ways to prevent SQL injection attacks. You can start by implementing input validation and role-based access controls. If you really want to ramp up your security, you can get a web application firewall and a vulnerability scanner.
Alternatively, you can install an all-in-one security plugin like Jetpack Security to get multiple security features bundled together. This includes real-time backups, a malware scanner, and anti-spam software. Sign up for Jetpack Security today!
We guard your site. You run your business.
Jetpack Security provides easy‑to‑use, comprehensive WordPress site security, including real‑time backups, a web application firewall, malware scanning, and spam protection.
Secure your site