Despite the latest technologies and best security practices, it’s still possible that your WordPress site gets hacked. This can quickly spiral if you don’t know how to recover your website.
The good news is that all hope isn’t lost after an attack. If you take the right steps — like contacting your hosting provider, identifying the cause of the hack, and restoring a clean backup — you can avoid a lot of pain and frustration.
In this post, we’ll take a look at the most common types of hacks that affect WordPress sites. Then, we’ll show you how to clean your hacked WordPress site and share some key methods to tighten security.
Common types of hacks that affect WordPress sites
Before we show you how to clean a hacked WordPress site, let’s first take a look at some of the most common types of attacks that affect WordPress.
1. Malware injection
Malware is rated as the most concerning type of cyber threat according to IT decision makers across the globe. The term is used to describe any type of harmful software, like ransomware or viruses, that can cause issues on your website or computer.
For example, the software might be able to take over your entire computer or account, monitor actions that you take on your site, or extract sensitive information (like personal or payment details). It can also be difficult to spot since it manifests itself in various ways.
Typically though, malware requires you to take an action in order to install or activate it. So, you might download a file or open an email attachment like an image or PDF document.
It can be very difficult to detect and remove malware from your website. Your best bet is to install a malware scanner like Jetpack Scan. But, if malware is discovered on your site, you’ll need to clean the affected files or replace them with copies from your backup files.
2. Brute force attacks
Brute force attacks occur when hackers use brute force to gain unauthorized access to your website. Using trial and error, hackers work through tons of password and username combinations until they succeed.
It’s one of the least sophisticated types of WordPress hacks. But, it’s still very popular since it can only take a few seconds to crack your password (depending on the length and complexity of it).
Typically, brute force attacks are conducted to carry out some other type of attack on your site. For instance, once the hacker makes their way through, they might distribute malware, steal personal data, reroute your website’s traffic, or place spam ads to make a profit.
Fortunately, you can reduce the likelihood of brute force attacks by hardening your login procedure. You might change the login URL, implement two-factor authentication, and enforce strong passwords. Plus, you can always use an automatic solution like Jetpack brute force protection.
3. SQL injection
The aim of a Structured Query Language (SQL) injection is to manipulate data out of your WordPress database. This can be accomplished by using SQL statements to trick the database into performing undesirable actions. Like many hacks, this type of attack can lead to further consequences.
For example, once the hacker gains access to your database, they might extract sensitive data, corrupt or modify information, bypass authentication, or delete all the data on your website. With access to your database tables and files, it’s also common for hackers to distribute malware in these locations.
To prevent SQL injections, you need to secure your database. This can usually be accomplished with a few simple things like keeping your database up-to-date to access the latest security updates. You should also limit database permissions, so that if a hacker does gain access, they’ll be able to do less damage.
4. Cross-site scripting (XSS)
Cross-site scripting (XSS), like malware, also involves malicious code being distributed on your site. But, in this instance, the code runs in the visitor’s browser when they land on your site.
Typically, the code is injected into comments, form fields, or scripts that might automatically run. For instance, the hacker may place malicious JavaScript into a comment on your WordPress blog.
One of the main issues with XSS attacks is that there’s usually no indication that anything has gone wrong. Additionally, since this type of attack targets your visitor’s information, it can significantly damage your website’s reputation.
Preventing XSS can be quite technical, but you’ll give yourself a better chance of reducing these attacks by implementing encryption protocols like SSL certificates. This way, even if a hacker can access the information, they won’t be able to read it.
5. Back doors
A back door attack bypasses the usual authentication procedures (like usernames and passwords) to gain unauthorized access to your site. To carry out this kind of attack, hackers exploit existing vulnerabilities or install malicious software to create an entry point.
Once the attackers find a way into your site, they’re able to steal information, track your activity, and disrupt your entire system. Unfortunately, an effective back door can go unnoticed for a very long time if it’s well hidden.
The best way to deter hackers from creating back doors on your site is to install a web application firewall (WAF) to monitor all incoming traffic. And pairing this with a malware scanner can help keep malicious content away from your site at the same time.
How WordPress sites get hacked
Now that you know a bit more about common types of hacks, let’s take a look at some of the ways that WordPress sites get hacked.
1. Outdated core, themes, and plugins
If you want to keep WordPress secure, it’s important to run core, theme, and plugin updates when they’re available. This is because most updates come with fixes for bugs and security vulnerabilities that have been discovered in the previous version.
Once these vulnerabilities are well-known, hackers can exploit them and use them to enter your website. Therefore, it’s always a good idea to update WordPress core, along with your themes and plugins, from your dashboard. And if you’re worried about updates breaking your site, you can create a backup to restore your website if something goes wrong.
2. Weak passwords and user credentials
The weaker your password, the easier it is for hackers to gain access to your website. In fact, even passwords that use numbers and symbols can be cracked in seconds if they’re less than seven characters long.
Additionally, most users tend to prioritize strong passwords for the WordPress admin account. But, it’s important to make all your passwords strong, including those you use for your web hosting account, FTP accounts, MySQL database, and email accounts.
Naturally, the easiest way to make your site less susceptible to a credential-based attack is to use (and enforce) strong passwords across your site. And, of course, you can harden the entire login procedure using methods like two-factor authentication.
3. A vulnerable hosting environment
Unless you run a local website, your site files are stored on a live server and open to attack. While there are numerous hosting providers available, it’s important to choose one that prioritizes WordPress and provides a secure environment.
That’s why it’s best to stick to reputable hosting providers that offer useful features like WAFs, SSL certificates, and auto-updates. Furthermore, if you have the budget, it’s usually safer to choose a managed hosting plan or dedicated hosting plan as opposed to a shared hosting environment.
4. Poorly coded themes and plugins
We’ve already discussed the importance of keeping your themes and plugins up-to-date. But, you should also make sure that you only install themes and plugins from trusted sources.
Typically, if you’re accessing new software for your site, it’s best to stick to the official WordPress directories, or the developer’s website (if it’s a premium tool). Plus, it’s always a good idea to check out the reviews to see if real users have encountered any security issues.
5. Insecure file uploads
Many websites let visitors upload files like resumes, images, and more. But a lot of WordPress users don’t realize that the file upload function can be used to carry out a number of serious attacks.
For instance, hackers may use the function to upload dangerous server-side script files that enable remote code execution or that can be triggered by an HTTP request.
Fortunately, you can prevent insecure file uploads by imposing file restrictions — including content type, file size, and more. Better yet, you can authenticate user sessions so that visitors need to log in before they can upload files on your site.
Common signs of a hacked WordPress site
Next, we’re going to take a look at the most common signs of an attack on your website.
1. Notifications from your security plugin
If you use a security plugin, you’ll know immediately if your WordPress site has been hacked. With Jetpack Scan, you’ll receive instant email notifications when threats or suspicious behavior is detected.
Better yet, when you visit your dashboard, the intuitive interface makes it easy to see and understand the issues that have been caught. And, some issues can even be resolved in just one click.
Scanning takes place on Jetpack servers so you can access your site even when it goes down.
The best part about using Jetpack as your WordPress security plugin is that you’re less likely to need to detect and remove malware in the first place. Thanks to its many protective measures — like a 24/7 WAF, two-factor authentication, brute force attack protection, and more — your site will be much harder for a hacker to access.
2. Suspicious file changes
One of the most common signs of a WordPress hack is suspicious file changes, particularly in your core WordPress files (and especially within the wp-content folder). This can be hard to spot since hackers may create new files with similar names to existing ones.
Or, they might simply modify your existing core files by placing their own code inside. Since this can be hard to detect, it’s important to use a security plugin that monitors your website files and database. If not, you’ll need to manually review WordPress folders to identify any malicious files or scripts.
3. Unfamiliar admin users or FTP accounts
If you’ve enabled user registration on your site (and you don’t use anti-spam protection), it’s easy for hackers to create spam user accounts. In this case, you’ll typically be able to simply delete the spam account.
But if your site isn’t open to user registration, and you’re seeing new user accounts, chances are that your website has been hacked. This is especially problematic if the new user is an administrator, since they’ll gain complete access to every part of your site.
4. Malicious redirects and pop-ups
Other common signs of a WordPress hack are malicious redirects and popups. In the latter case, hackers attempt to hijack your web traffic and make money by displaying spam ads.
While these types of popups won’t appear for logged-in users or those that visit your website directly, they’ll be visible to those that land on your site from search engines. What’s worse, these ads often open in a new window and can go unnoticed for a long time.
Additionally, hackers may re-route your website’s traffic to third-party websites which may distribute malware or cause other security risks. Usually, this kind of attack is caused by a back door on your site that hackers can exploit.
5. Links to spam sites
As we discussed in an earlier section, data injections are one of the most common types of WordPress security issues. And once a hacker gains access to your site (usually through a back door), they’re able to modify files and tables in your database.
Some of these hacks involve links to spam websites which are often added to the WordPress footer. And while you can delete the links you find, this won’t resolve the root of the problem. Instead, you’ll need to find and fix the back door that hackers were able to exploit.
6. Unusual traffic spikes
Changes to your usual web traffic can often be a clear indicator of a WordPress hack. For example, a sudden drop in traffic might mean that malware on your site is redirecting visitors to spam websites.
Meanwhile, if your server is flooded with tons of requests, it might be the case that hackers are attempting a distributed denial of service attack (DDoS). In this instance, hackers overwhelm your server with hundreds of fake requests to cause your website to crash.
7. Google blocklisting
Another reason for a drop in web traffic could be that Google’s safe browsing tool is warning visitors against accessing your website. In fact, Google blocklists about 10,000 websites every day due to irregularities that it believes to be malware, phishing links, spam, and more.
In this case, your website will be removed from the Google index and visitors won’t be able to view or use your website. This can also damage your website’s reputation since it makes your site seem untrustworthy and unsafe.
You can view your site’s safety report using the safe browsing tool. To remove your site from the blocklist, you’ll need to address the issues. Then, you can use Google Search Console to request a security review.
We guard your site. You run your business.
Jetpack Security provides easy‑to‑use, comprehensive WordPress site security, including real‑time backups, a web application firewall, malware scanning, and spam protection.
Secure your siteUsing Jetpack Scan to detect security issues
The best way to prevent your WordPress site from getting hacked is to use an automatic security feature like Jetpack Scan. This way, you’ll get daily malware and vulnerability scans and immediate alerts whenever issues are discovered. Plus, you’ll receive advice about how to resolve problems and gain access to one-click fixes.
Jetpack Scan is available as a standalone feature or as part of the Security plan with the Jetpack Plugin. Jetpack Security is the best option because it includes Jetpack Scan, but also includes real-time backups, spam protection, two-factor authentication, brute force attack protection, and a comprehensive 30-day activity log to track all actions on your site.
If you don’t want the full Jetpack plugin, you can opt for a paid plan with the Jetpack Protect plugin to get the same access to free daily malware scans, instant alerts, and one-click fixes. Plus, you’ll also get 24/7 WAF protection.
1. Identify the source of the hack
If you’re wondering how to clean a hacked WordPress site, the first step is to identify the source of the hack. The easiest way to do this is to consult an activity log (as long as you have a security plugin that provides one).
For instance, with Jetpack Security, you’ll gain a 30-day activity log where you can monitor every action on your site. This includes everything from new user accounts to file modifications. That means you’ll be able to review all listed actions and take note of anything that seems suspicious.
If you don’t have an activity log, or you can’t access your site, it’s a good idea to check your server error logs. You can only access error logs by enabling debugging in WordPress.
You can do this using a plugin like WP Debugging.
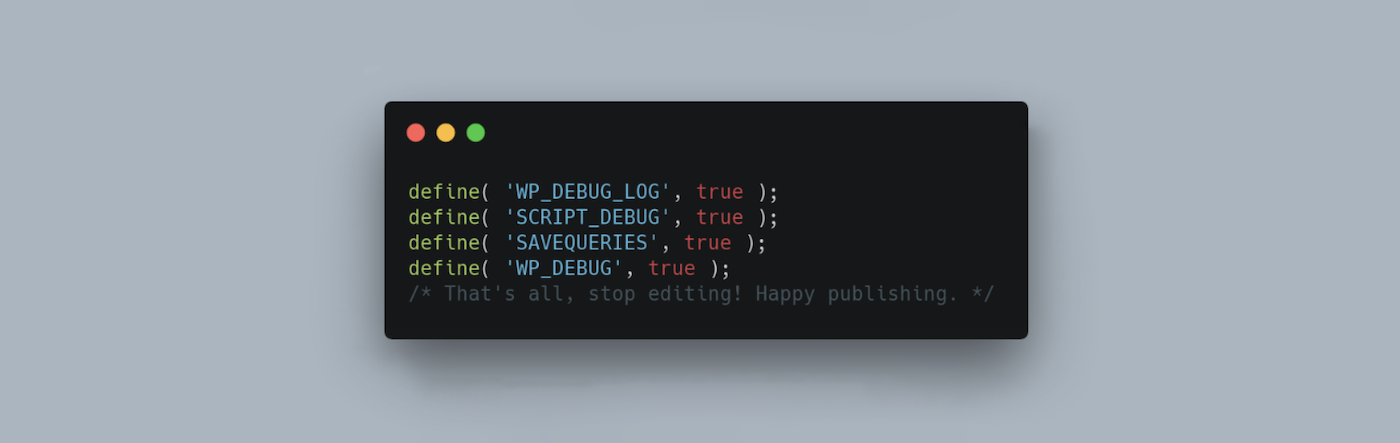
Or, you can edit your wp-config.php file via an FTP client. In this instance, find the line that reads “That’s all, stop editing!” Then, paste the following code:
define( 'WP_DEBUG', true );
define( 'WP_DEBUG_LOG', true );The error log is usually called debug.log and can be found within the wp-content folder. Here, you can view all error messages, warnings, and notices that have been logged on your site.
But keep in mind that directly modifying your website’s files is a very delicate process. As such, only advanced WordPress users or developers should attempt it. And you should always have a full backup of your site on-hand before proceeding.
As a simpler alternative, you can install a malware scanner like Jetpack Scan to detect malware on your site.
2. Contact your hosting provider
The next step to clean a hacked WordPress site is to contact your hosting provider. This is especially relevant if you use a shared hosting plan since there may be a larger issue that your host is already aware of. Additionally, depending on your hosting type, you may not be able to access your server error logs. So in this instance, you’ll need to ask your host to do this for you.
3. Restore a clean backup if you have one
The good news is that if you have a backup on hand, it’s much easier to clean a hacked WordPress site. That’s because you’ll be able to simply revert your website back to a previous version.
Naturally, you’re only able to do this if you use a backup plugin like Jetpack VaultPress Backup.
This is a sophisticated plugin that creates real-time cloud backups of your site, including database tables, content, and WooCommerce data. Backups are also encrypted to keep your information safe. And, you’ll benefit from one-click restores, which you can do from your site or the mobile app — even if your site is fully down.
All you have to do is head to Jetpack → Activity Log and use the filters to search for a specific date range or event. Then, click on Restore. Alternatively, you can go to Jetpack → Backup → Actions → Restore to this point.
If you want to restore your whole site, leave all boxes checked and select Confirm restore. You’ll then receive a confirmation message when the process is complete.
4. Clean hacked files
Lastly, if you’re wondering how to clean a hacked WordPress site, and you don’t have a backup on hand, you’ll need to clean the targeted files. But, before you begin, it’s important to create a backup of your site in case anything goes wrong when you remove/edit the files.
If you’re using a security plugin or malware scanner, you can review the reports that may provide a list of suspicious files. For example, Jetpack Scan offers one-click fixes for many common errors and hacks.
Or if you’re doing this manually, you can download a fresh WordPress installation and compare the code in the core files with your website files. If you find any code that doesn’t fit with the new files, go ahead and remove it.
Alternatively, you can replace all WordPress files by going to Dashboard → Updates and clicking on the Re-install version button.
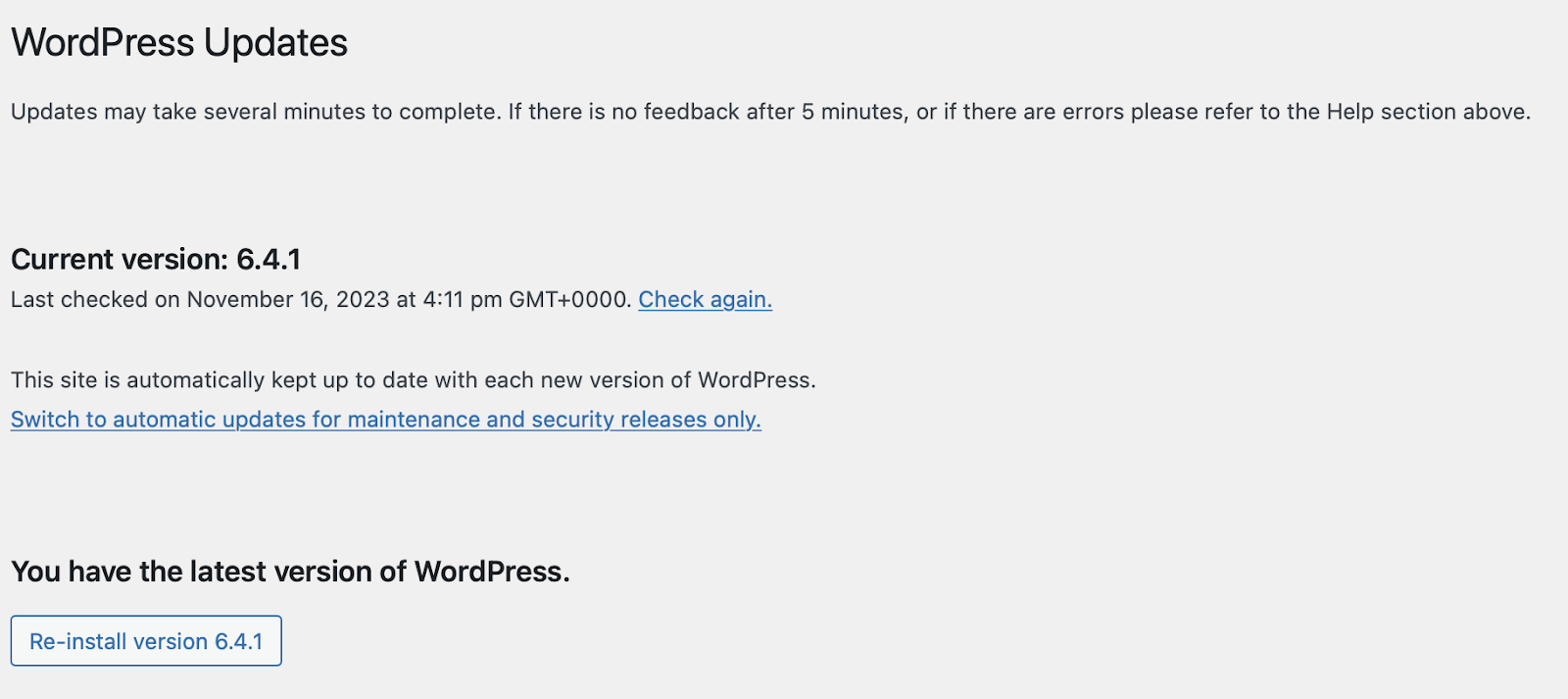
This won’t replace or delete any content, plugins, or images. All it does is replace the files at the core of WordPress.
Additionally, if the affected files are in your WordPress theme, simply uninstall the theme and then install a fresh version. The same goes for any infected plugin files.
Tightening security after cleaning your hacked site
Now that you know how to clean a hacked WordPress site, let’s run through some methods to tighten security following the cleanup. This way, you can better protect your website from future hacks.
1. Install a security and backup plugin
The most effortless way to extend protection for your WordPress site is to install a security and backup plugin. This will provide protection from the majority of threats, as well as solutions to solve most problems that slip through.
The best WordPress security plugins offer a range of preventative measures like WAFs, daily scans, activity logs, and login protection. You can also find options like Jetpack Security that even include follow-up care like recommended actions and one-click fixes.
Better yet, Jetpack Security includes the advanced Jetpack VaultPress Backup plugin so you don’t need to install a separate service. This way, you can make real-time copies of all files and database tables on hand. Plus, you can restore certain elements, or your entire site, in just one click.
2. Reset all passwords
If your WordPress website has been hacked, there’s a good chance that your passwords have been compromised. Therefore, you should reset all passwords including those for your admin account, hosting account, FTP account, email account, and database.
To strengthen your login procedure, it’s best to stick with very strong passwords that consist of uppercase and lowercase letters, numbers, and special characters. Plus, aim to make passwords as long as possible. If you can’t come up with strong passwords yourself, you can always use a password generator.
3. Implement strong password policies
Although it’s useful to reset your passwords, you’ll also want to implement strong password policies across your site to protect all user accounts. This can involve educating users about the dangers of weak passwords.
With this in mind, you might want to include this information in a welcome email when new users register on your site. Or you can enforce strong passwords with a plugin like Password Policy Manager.

This way, you can monitor the password strength of all passwords. You can also require users to change their existing passwords and enable auto expiry dates to require regular credential updates.
4. Set up two-factor authentication (2FA) with Jetpack
While strong passwords can make it difficult for hackers to gain access to your site, you can go one step further and implement two-factor authentication. This way, in addition to a strong password, users will need a second key to successfully log in.
Typically, the second key is a verification code that is sent to an email account or mobile phone number. The good news is that if you’re already using a security plugin like Jetpack, you can enable this directly within your dashboard.
All you have to do is go to Jetpack → Settings → Security. Locate the WordPress.com login section and use the toggle button to allow users to log into your site with their WordPress.com accounts. Then, use the toggle below to require accounts to use two-factor authentication.
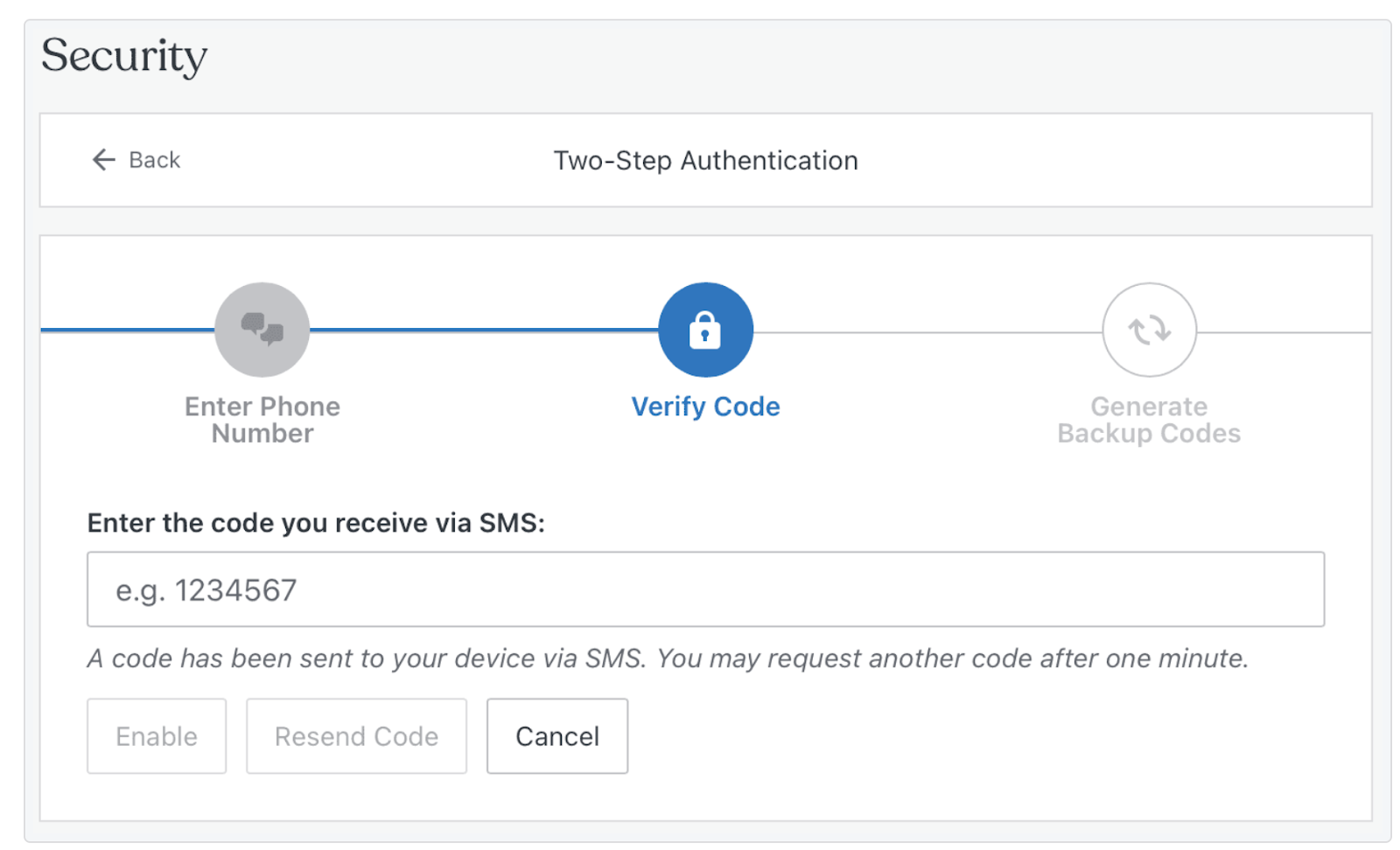
5. Keep WordPress software up-to-date
One of the simplest ways to harden WordPress security is to regularly update the core WordPress software (as well as themes and plugins). This way, you’ll get access to the latest security patches. Plus, it makes your site more resilient to back door attacks.
To make sure you’re running the latest version of WordPress, go to Dashboard → Updates. Below here, you’ll also see the plugins and themes that have updates available. Simply select the relevant options and click on Update.
6. Audit user accounts
It’s important to make sure that the right people have the right level of access to your website. To determine this, you’ll need to assign user roles to each new user on your website. This grants specific permissions and privileges to each registered person.
But, it’s a good idea to regularly audit your user accounts to make sure the settings reflect the current state of your website. For instance, you may forget to delete a user when a staff member resigns.
You can view all user roles by going to Users → All Users within your WordPress dashboard. At the top of the page, you’ll see links where you can view accounts according to their user role, like authors, contributors, and editors.
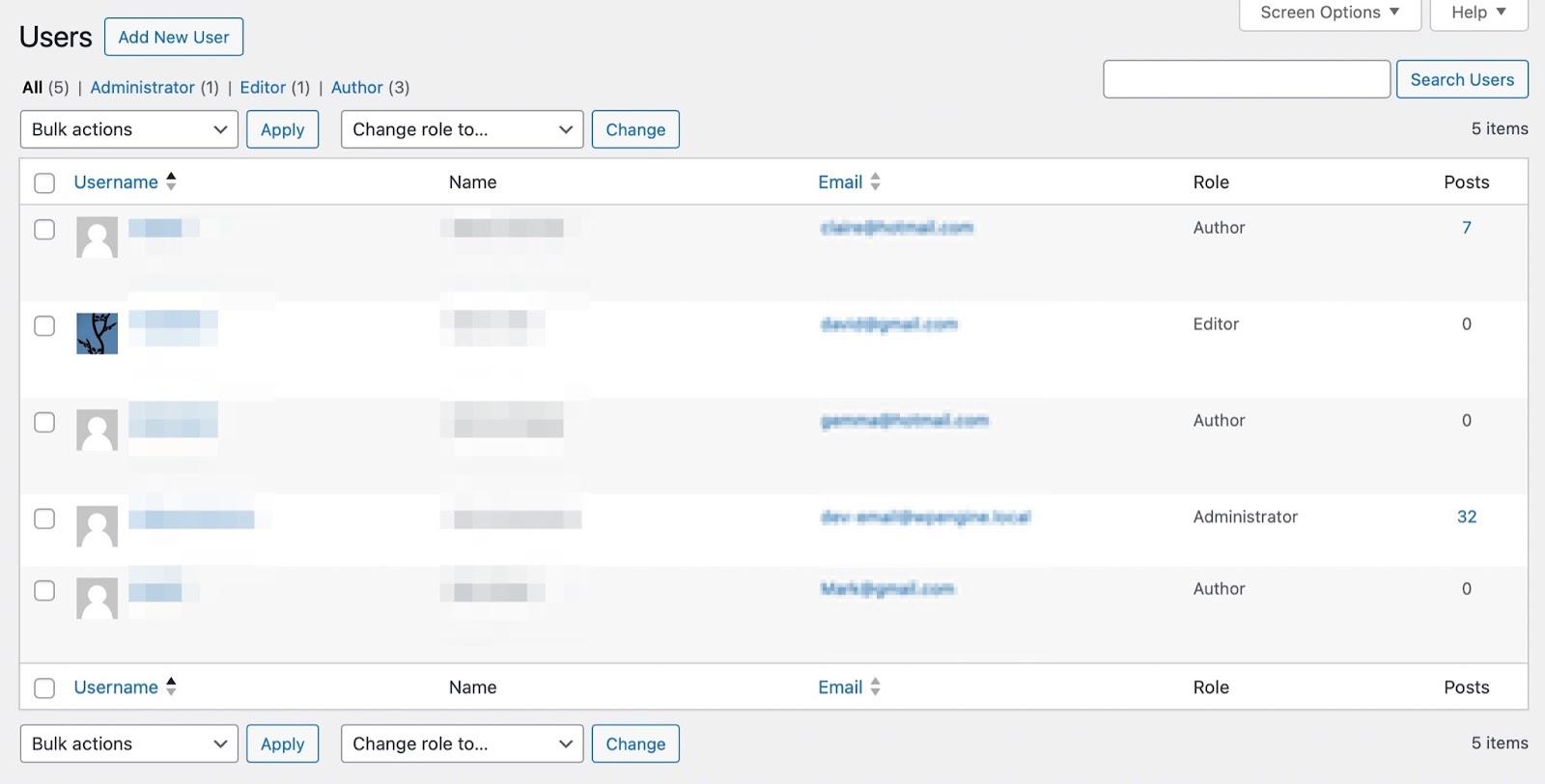
As a general rule, each site should only have one administrator. If you see new administrator accounts, this may be a sign of a hack. Additionally, it’s best to operate on the principle of least privilege so that users can only perform actions that they absolutely need to.
7. Remove your site from unsafe lists (Google or McAfee)
If your website has fallen victim to a WordPress hack, you might find that you’ve been blocklisted by search engines like Google and McAfee. Even once you’ve cleaned the infected files (or restored your site), you will likely still see warnings.
In this instance, you’ll need to request a security review to remove your site from unsafe lists. You can do this using Google Search Console. And, you can also submit a dispute request with McAfee.
How to hack-proof your site with Jetpack Security
As we discussed, the best way to hack-proof your website is to install a complete security solution like Jetpack Security.
To get started with this tool, start by installing and activating the Jetpack plugin. Then, all you need to do is select a Security or Complete plan and proceed to checkout. Enter the URL for your site and continue. You’ll also need to input the admin credentials for the account that you want to connect to Jetpack.
Once Jetpack is set up successfully, you’ll be able to complete the checkout process. Then, you can enable the recommended features in the setup checklist. Or, return to your dashboard and configure the settings at a later date.
Frequently asked questions
In this section, we’ll address some of the most frequently asked questions about cleaning and securing a hacked WordPress site.
How can I be sure that my WordPress site has been hacked?
The best way to know that your WordPress site has been hacked is to consult your security plugin. With a quality plugin like Jetpack, you’ll receive instant email notifications when a threat is detected.
But there are some other common signs of a hack that you can look out for. For instance, you may discover unfamiliar user accounts or FTP accounts.
Additionally, there might be new links to third-party websites or suspicious changes to important WordPress files. And if your website has been hacked, you may find it on blocklists for Google and McAfee.
How can I scan my WordPress site for malware?
Malware is one of the most concerning online threats, and it can be very difficult to identify. Fortunately, you can use a simple scanning tool like Jetpack Scan, which will automatically review your site for vulnerabilities and malware and instantly alert you if a problem is detected.
Plus, it comes with one-click fixes for most issues and a 24/7 WAF to block malicious traffic to reduce threats from the start.
Why is it important to regularly back up my WordPress site?
If your WordPress site gets hacked, it’s not the end of the world if you have backups in place. If you don’t, you may encounter a lot more trouble as you’ll have to manually review all your website files for malicious code. Then, you’ll need to replace any corrupted files with clean replacements, which can be time-consuming and error-prone.
But, with a tool like Jetpack VaultPress Backup, you’re able to revert your website to an earlier version right away. You can choose the exact point in time that you’d like to restore your website to. Plus, you can choose to restore your entire website or select specific files.
What is the best way to back up my WordPress site?
The simplest way to back up your website is to install an automatic plugin like Jetpack VaultPress Backup. This way, you can protect your website files, database tables, and customer and order data.
Backups are stored in the cloud, so even if your server crashes, your backup will remain intact. What’s more, the restoration process is super easy, with the option to restore your site in just a click. Plus, you can do this directly from your dashboard or use the Jetpack mobile app.
What is a web application firewall (WAF) and how does it improve WordPress security?
A web application firewall (WAF) is one of the most sophisticated preventative security measures that you can implement on your site. A WAF works by monitoring all your incoming web traffic. Then, it blocks any IP address that it deems suspicious.
If you opt to protect your site with Jetpack Security, you’ll get access to a WAF for 24/7 protection.
How does Jetpack Security help in identifying and mitigating hacking attempts?
Jetpack Security can give you total peace of mind when it comes to WordPress security. You’ll get access to real-time backups, so if anything goes wrong on your site, you can quickly restore it back to an earlier version.
Jetpack provides comment and form spam protection with Akismet. And you’ll even get a 30-day activity log where you can monitor every action on your site. This is especially useful when identifying errors and other security problems.
What’s more, you’ll also gain malware scans and a WAF. Plus, when issues are detected on your site, you’ll be notified immediately. And, through your dashboard, you’ll gain access to one-click fixes and expert security recommendations.
Jetpack Security: Your shield against WordPress hacks
It’s easy to panic when you realize that your WordPress site has been hacked. This is especially true when you have no idea how to recover your website. But the situation is much less stressful when you know how to clean and hack-proof your site.
Once you’ve restored your site using a backup (or cleaned the hacked files), you can install a security plugin and reset all passwords. Then, it’s important to audit user accounts, set up two-factor authentication, and remove your site from all blocklists.
But for total peace of mind, it’s a good idea to install an all-in-one security plugin like Jetpack Security. This way, you’ll get access to a 30-day activity log, full comment and form spam protection, real-time backups, brute force attack protection, a web application firewall, and more. Get started today to secure your WordPress site!
We guard your site. You run your business.
Jetpack Security provides easy‑to‑use, comprehensive WordPress site security, including real‑time backups, a web application firewall, malware scanning, and spam protection.
Secure your site